Replace 'userxx' with 'orgxx' in all test files when the user type is org (#27052)
Currently 'userxx' and 'orgxx' are both used as username in test files when the user type is org, which is confusing. This PR replaces all 'userxx' with 'orgxx' when the user type is org(`user.type==1`). Some non-trivial changes 1. Rename `user3` dir to `org3` in `tests/git-repositories-meta` 2. Change `end` in `issue reference` because 'org3' is one char shorter than 'user3' 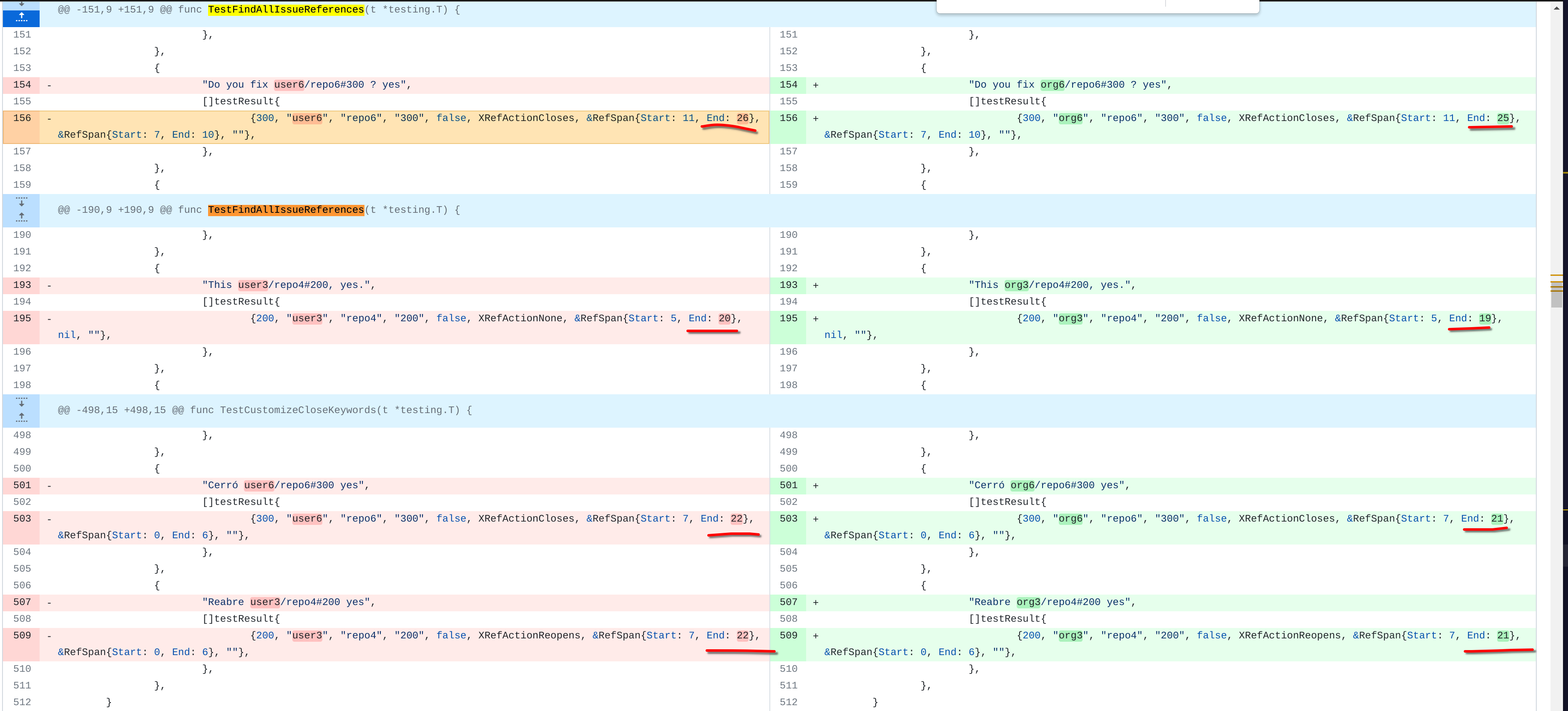 3. Change the search result number of `user/repo2` because `user3/repo21` can't be searched now 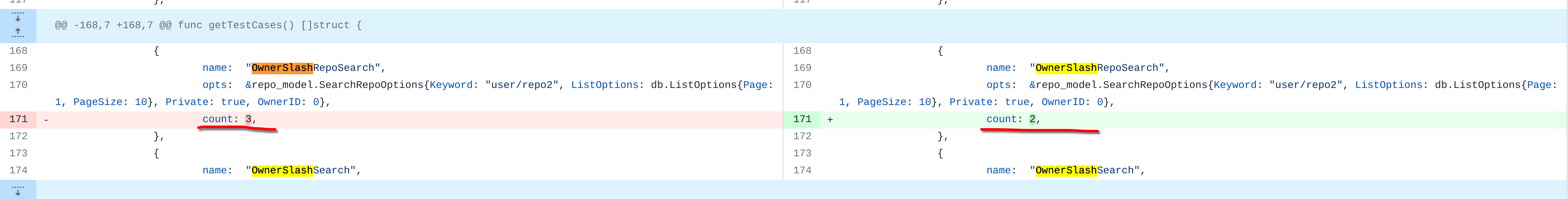 4. Change the first org name getting from API because the result is ordered by alphabet asc and now `org 17` is before `org25`  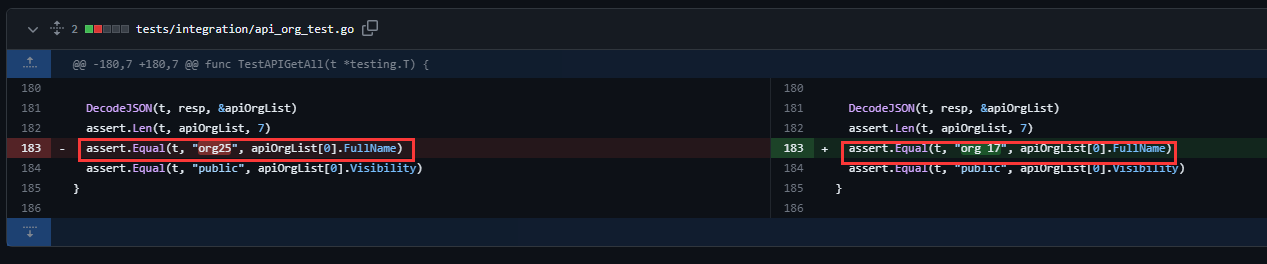 Other modifications are just find all and replace all. Unit tests with SQLite are all passed. --------- Co-authored-by: caicandong <1290147055@qq.com>
This commit is contained in:
parent
d0318c4ae0
commit
da50be7360
91 changed files with 280 additions and 280 deletions
|
|
@ -73,8 +73,8 @@
|
|||
-
|
||||
id: 10
|
||||
uid: 3
|
||||
email: user3@example.com
|
||||
lower_email: user3@example.com
|
||||
email: org3@example.com
|
||||
lower_email: org3@example.com
|
||||
is_activated: true
|
||||
is_primary: true
|
||||
|
||||
|
|
@ -97,16 +97,16 @@
|
|||
-
|
||||
id: 13
|
||||
uid: 6
|
||||
email: user6@example.com
|
||||
lower_email: user6@example.com
|
||||
email: org6@example.com
|
||||
lower_email: org6@example.com
|
||||
is_activated: true
|
||||
is_primary: true
|
||||
|
||||
-
|
||||
id: 14
|
||||
uid: 7
|
||||
email: user7@example.com
|
||||
lower_email: user7@example.com
|
||||
email: org7@example.com
|
||||
lower_email: org7@example.com
|
||||
is_activated: true
|
||||
is_primary: true
|
||||
|
||||
|
|
@ -153,8 +153,8 @@
|
|||
-
|
||||
id: 20
|
||||
uid: 17
|
||||
email: user17@example.com
|
||||
lower_email: user17@example.com
|
||||
email: org17@example.com
|
||||
lower_email: org17@example.com
|
||||
is_activated: true
|
||||
is_primary: true
|
||||
|
||||
|
|
@ -169,8 +169,8 @@
|
|||
-
|
||||
id: 22
|
||||
uid: 19
|
||||
email: user19@example.com
|
||||
lower_email: user19@example.com
|
||||
email: org19@example.com
|
||||
lower_email: org19@example.com
|
||||
is_activated: true
|
||||
is_primary: true
|
||||
|
||||
|
|
|
|||
|
|
@ -64,7 +64,7 @@
|
|||
-
|
||||
id: 3
|
||||
owner_id: 3
|
||||
owner_name: user3
|
||||
owner_name: org3
|
||||
lower_name: repo3
|
||||
name: repo3
|
||||
default_branch: master
|
||||
|
|
@ -126,7 +126,7 @@
|
|||
-
|
||||
id: 5
|
||||
owner_id: 3
|
||||
owner_name: user3
|
||||
owner_name: org3
|
||||
lower_name: repo5
|
||||
name: repo5
|
||||
num_watches: 0
|
||||
|
|
@ -671,7 +671,7 @@
|
|||
-
|
||||
id: 23
|
||||
owner_id: 17
|
||||
owner_name: user17
|
||||
owner_name: org17
|
||||
lower_name: big_test_public_4
|
||||
name: big_test_public_4
|
||||
num_watches: 0
|
||||
|
|
@ -701,7 +701,7 @@
|
|||
-
|
||||
id: 24
|
||||
owner_id: 17
|
||||
owner_name: user17
|
||||
owner_name: org17
|
||||
lower_name: big_test_private_4
|
||||
name: big_test_private_4
|
||||
num_watches: 0
|
||||
|
|
@ -791,7 +791,7 @@
|
|||
-
|
||||
id: 27
|
||||
owner_id: 19
|
||||
owner_name: user19
|
||||
owner_name: org19
|
||||
lower_name: big_test_public_mirror_6
|
||||
name: big_test_public_mirror_6
|
||||
num_watches: 0
|
||||
|
|
@ -821,7 +821,7 @@
|
|||
-
|
||||
id: 28
|
||||
owner_id: 19
|
||||
owner_name: user19
|
||||
owner_name: org19
|
||||
lower_name: big_test_private_mirror_6
|
||||
name: big_test_private_mirror_6
|
||||
num_watches: 0
|
||||
|
|
@ -942,7 +942,7 @@
|
|||
-
|
||||
id: 32 # org public repo
|
||||
owner_id: 3
|
||||
owner_name: user3
|
||||
owner_name: org3
|
||||
lower_name: repo21
|
||||
name: repo21
|
||||
num_watches: 0
|
||||
|
|
|
|||
|
|
@ -129,6 +129,6 @@
|
|||
type: 1
|
||||
reviewer_id: 6
|
||||
issue_id: 11
|
||||
content: "singular review from user6 and final review for this pr"
|
||||
content: "singular review from org6 and final review for this pr"
|
||||
updated_unix: 946684831
|
||||
created_unix: 946684831
|
||||
|
|
|
|||
|
|
@ -76,17 +76,17 @@
|
|||
|
||||
-
|
||||
id: 3
|
||||
lower_name: user3
|
||||
name: user3
|
||||
lower_name: org3
|
||||
name: org3
|
||||
full_name: ' <<<< >> >> > >> > >>> >> '
|
||||
email: user3@example.com
|
||||
email: org3@example.com
|
||||
keep_email_private: false
|
||||
email_notifications_preference: onmention
|
||||
passwd: ZogKvWdyEx:password
|
||||
passwd_hash_algo: dummy
|
||||
must_change_password: false
|
||||
login_source: 0
|
||||
login_name: user3
|
||||
login_name: org3
|
||||
type: 1
|
||||
salt: ZogKvWdyEx
|
||||
max_repo_creation: -1
|
||||
|
|
@ -98,7 +98,7 @@
|
|||
allow_create_organization: true
|
||||
prohibit_login: false
|
||||
avatar: avatar3
|
||||
avatar_email: user3@example.com
|
||||
avatar_email: org3@example.com
|
||||
use_custom_avatar: false
|
||||
num_followers: 0
|
||||
num_following: 0
|
||||
|
|
@ -187,17 +187,17 @@
|
|||
|
||||
-
|
||||
id: 6
|
||||
lower_name: user6
|
||||
name: user6
|
||||
full_name: User Six
|
||||
email: user6@example.com
|
||||
lower_name: org6
|
||||
name: org6
|
||||
full_name: Org Six
|
||||
email: org6@example.com
|
||||
keep_email_private: false
|
||||
email_notifications_preference: enabled
|
||||
passwd: ZogKvWdyEx:password
|
||||
passwd_hash_algo: dummy
|
||||
must_change_password: false
|
||||
login_source: 0
|
||||
login_name: user6
|
||||
login_name: org6
|
||||
type: 1
|
||||
salt: ZogKvWdyEx
|
||||
max_repo_creation: -1
|
||||
|
|
@ -209,7 +209,7 @@
|
|||
allow_create_organization: true
|
||||
prohibit_login: false
|
||||
avatar: avatar6
|
||||
avatar_email: user6@example.com
|
||||
avatar_email: org6@example.com
|
||||
use_custom_avatar: false
|
||||
num_followers: 0
|
||||
num_following: 0
|
||||
|
|
@ -224,17 +224,17 @@
|
|||
|
||||
-
|
||||
id: 7
|
||||
lower_name: user7
|
||||
name: user7
|
||||
full_name: User Seven
|
||||
email: user7@example.com
|
||||
lower_name: org7
|
||||
name: org7
|
||||
full_name: Org Seven
|
||||
email: org7@example.com
|
||||
keep_email_private: false
|
||||
email_notifications_preference: disabled
|
||||
passwd: ZogKvWdyEx:password
|
||||
passwd_hash_algo: dummy
|
||||
must_change_password: false
|
||||
login_source: 0
|
||||
login_name: user7
|
||||
login_name: org7
|
||||
type: 1
|
||||
salt: ZogKvWdyEx
|
||||
max_repo_creation: -1
|
||||
|
|
@ -246,7 +246,7 @@
|
|||
allow_create_organization: true
|
||||
prohibit_login: false
|
||||
avatar: avatar7
|
||||
avatar_email: user7@example.com
|
||||
avatar_email: org7@example.com
|
||||
use_custom_avatar: false
|
||||
num_followers: 0
|
||||
num_following: 0
|
||||
|
|
@ -594,17 +594,17 @@
|
|||
|
||||
-
|
||||
id: 17
|
||||
lower_name: user17
|
||||
name: user17
|
||||
full_name: User 17
|
||||
email: user17@example.com
|
||||
lower_name: org17
|
||||
name: org17
|
||||
full_name: org 17
|
||||
email: org17@example.com
|
||||
keep_email_private: false
|
||||
email_notifications_preference: enabled
|
||||
passwd: ZogKvWdyEx:password
|
||||
passwd_hash_algo: dummy
|
||||
must_change_password: false
|
||||
login_source: 0
|
||||
login_name: user17
|
||||
login_name: org17
|
||||
type: 1
|
||||
salt: ZogKvWdyEx
|
||||
max_repo_creation: -1
|
||||
|
|
@ -616,7 +616,7 @@
|
|||
allow_create_organization: true
|
||||
prohibit_login: false
|
||||
avatar: avatar17
|
||||
avatar_email: user17@example.com
|
||||
avatar_email: org17@example.com
|
||||
use_custom_avatar: false
|
||||
num_followers: 0
|
||||
num_following: 0
|
||||
|
|
@ -668,17 +668,17 @@
|
|||
|
||||
-
|
||||
id: 19
|
||||
lower_name: user19
|
||||
name: user19
|
||||
full_name: User 19
|
||||
email: user19@example.com
|
||||
lower_name: org19
|
||||
name: org19
|
||||
full_name: Org 19
|
||||
email: org19@example.com
|
||||
keep_email_private: false
|
||||
email_notifications_preference: enabled
|
||||
passwd: ZogKvWdyEx:password
|
||||
passwd_hash_algo: dummy
|
||||
must_change_password: false
|
||||
login_source: 0
|
||||
login_name: user19
|
||||
login_name: org19
|
||||
type: 1
|
||||
salt: ZogKvWdyEx
|
||||
max_repo_creation: -1
|
||||
|
|
@ -690,7 +690,7 @@
|
|||
allow_create_organization: true
|
||||
prohibit_login: false
|
||||
avatar: avatar19
|
||||
avatar_email: user19@example.com
|
||||
avatar_email: org19@example.com
|
||||
use_custom_avatar: false
|
||||
num_followers: 0
|
||||
num_following: 0
|
||||
|
|
|
|||
|
|
@ -27,9 +27,9 @@ func TestUpdateAssignee(t *testing.T) {
|
|||
_, _, err = issues_model.ToggleIssueAssignee(db.DefaultContext, issue, &user_model.User{ID: 1}, user2.ID)
|
||||
assert.NoError(t, err)
|
||||
|
||||
user3, err := user_model.GetUserByID(db.DefaultContext, 3)
|
||||
org3, err := user_model.GetUserByID(db.DefaultContext, 3)
|
||||
assert.NoError(t, err)
|
||||
_, _, err = issues_model.ToggleIssueAssignee(db.DefaultContext, issue, &user_model.User{ID: 1}, user3.ID)
|
||||
_, _, err = issues_model.ToggleIssueAssignee(db.DefaultContext, issue, &user_model.User{ID: 1}, org3.ID)
|
||||
assert.NoError(t, err)
|
||||
|
||||
user1, err := user_model.GetUserByID(db.DefaultContext, 1) // This user is already assigned (see the definition in fixtures), so running UpdateAssignee should unassign him
|
||||
|
|
@ -47,7 +47,7 @@ func TestUpdateAssignee(t *testing.T) {
|
|||
assert.NoError(t, err)
|
||||
|
||||
var expectedAssignees []*user_model.User
|
||||
expectedAssignees = append(expectedAssignees, user2, user3)
|
||||
expectedAssignees = append(expectedAssignees, user2, org3)
|
||||
|
||||
for in, assignee := range issue.Assignees {
|
||||
assert.Equal(t, assignee.ID, expectedAssignees[in].ID)
|
||||
|
|
|
|||
|
|
@ -430,11 +430,11 @@ func TestIssue_ResolveMentions(t *testing.T) {
|
|||
// Public repo, doer
|
||||
testSuccess("user2", "repo1", "user1", []string{"user1"}, []int64{})
|
||||
// Private repo, team member
|
||||
testSuccess("user17", "big_test_private_4", "user20", []string{"user2"}, []int64{2})
|
||||
testSuccess("org17", "big_test_private_4", "user20", []string{"user2"}, []int64{2})
|
||||
// Private repo, not a team member
|
||||
testSuccess("user17", "big_test_private_4", "user20", []string{"user5"}, []int64{})
|
||||
testSuccess("org17", "big_test_private_4", "user20", []string{"user5"}, []int64{})
|
||||
// Private repo, whole team
|
||||
testSuccess("user17", "big_test_private_4", "user15", []string{"user17/owners"}, []int64{18})
|
||||
testSuccess("org17", "big_test_private_4", "user15", []string{"org17/owners"}, []int64{18})
|
||||
}
|
||||
|
||||
func TestResourceIndex(t *testing.T) {
|
||||
|
|
|
|||
|
|
@ -54,7 +54,7 @@ func TestXRef_AddCrossReferences(t *testing.T) {
|
|||
itarget = testCreateIssue(t, 3, 3, "title4", "content4", false)
|
||||
|
||||
// Cross-reference to issue #4 by admin
|
||||
content = fmt.Sprintf("content5, mentions user3/repo3#%d", itarget.Index)
|
||||
content = fmt.Sprintf("content5, mentions org3/repo3#%d", itarget.Index)
|
||||
i = testCreateIssue(t, 2, 1, "title5", content, false)
|
||||
ref = unittest.AssertExistsAndLoadBean(t, &issues_model.Comment{IssueID: itarget.ID, RefIssueID: i.ID, RefCommentID: 0})
|
||||
assert.Equal(t, issues_model.CommentTypeIssueRef, ref.Type)
|
||||
|
|
@ -63,7 +63,7 @@ func TestXRef_AddCrossReferences(t *testing.T) {
|
|||
assert.Equal(t, references.XRefActionNone, ref.RefAction)
|
||||
|
||||
// Cross-reference to issue #4 with no permission
|
||||
content = fmt.Sprintf("content6, mentions user3/repo3#%d", itarget.Index)
|
||||
content = fmt.Sprintf("content6, mentions org3/repo3#%d", itarget.Index)
|
||||
i = testCreateIssue(t, 4, 5, "title6", content, false)
|
||||
unittest.AssertNotExistsBean(t, &issues_model.Comment{IssueID: itarget.ID, RefIssueID: i.ID, RefCommentID: 0})
|
||||
}
|
||||
|
|
|
|||
|
|
@ -317,9 +317,9 @@ func TestParseCodeOwnersLine(t *testing.T) {
|
|||
{Line: "# comment", Tokens: []string{}},
|
||||
{Line: "!.* @user1 @org1/team1", Tokens: []string{"!.*", "@user1", "@org1/team1"}},
|
||||
{Line: `.*\\.js @user2 #comment`, Tokens: []string{`.*\.js`, "@user2"}},
|
||||
{Line: `docs/(aws|google|azure)/[^/]*\\.(md|txt) @user3 @org2/team2`, Tokens: []string{`docs/(aws|google|azure)/[^/]*\.(md|txt)`, "@user3", "@org2/team2"}},
|
||||
{Line: `\#path @user3`, Tokens: []string{`#path`, "@user3"}},
|
||||
{Line: `path\ with\ spaces/ @user3`, Tokens: []string{`path with spaces/`, "@user3"}},
|
||||
{Line: `docs/(aws|google|azure)/[^/]*\\.(md|txt) @org3 @org2/team2`, Tokens: []string{`docs/(aws|google|azure)/[^/]*\.(md|txt)`, "@org3", "@org2/team2"}},
|
||||
{Line: `\#path @org3`, Tokens: []string{`#path`, "@org3"}},
|
||||
{Line: `path\ with\ spaces/ @org3`, Tokens: []string{`path with spaces/`, "@org3"}},
|
||||
}
|
||||
|
||||
for _, g := range given {
|
||||
|
|
@ -335,7 +335,7 @@ func TestGetApprovers(t *testing.T) {
|
|||
// to assert that there are no duplicated approvers.
|
||||
setting.Repository.PullRequest.DefaultMergeMessageOfficialApproversOnly = false
|
||||
approvers := pr.GetApprovers()
|
||||
expected := "Reviewed-by: User Five <user5@example.com>\nReviewed-by: User Six <user6@example.com>\n"
|
||||
expected := "Reviewed-by: User Five <user5@example.com>\nReviewed-by: Org Six <org6@example.com>\n"
|
||||
assert.EqualValues(t, expected, approvers)
|
||||
}
|
||||
|
||||
|
|
|
|||
|
|
@ -83,7 +83,7 @@ func TestIssueReactionCount(t *testing.T) {
|
|||
|
||||
user1 := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 1})
|
||||
user2 := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 2})
|
||||
user3 := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 3})
|
||||
org3 := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 3})
|
||||
user4 := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 4})
|
||||
ghost := user_model.NewGhostUser()
|
||||
|
||||
|
|
@ -92,8 +92,8 @@ func TestIssueReactionCount(t *testing.T) {
|
|||
|
||||
addReaction(t, user1.ID, issueID, 0, "heart")
|
||||
addReaction(t, user2.ID, issueID, 0, "heart")
|
||||
addReaction(t, user3.ID, issueID, 0, "heart")
|
||||
addReaction(t, user3.ID, issueID, 0, "+1")
|
||||
addReaction(t, org3.ID, issueID, 0, "heart")
|
||||
addReaction(t, org3.ID, issueID, 0, "+1")
|
||||
addReaction(t, user4.ID, issueID, 0, "+1")
|
||||
addReaction(t, user4.ID, issueID, 0, "heart")
|
||||
addReaction(t, ghost.ID, issueID, 0, "-1")
|
||||
|
|
@ -136,7 +136,7 @@ func TestIssueCommentDeleteReaction(t *testing.T) {
|
|||
|
||||
user1 := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 1})
|
||||
user2 := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 2})
|
||||
user3 := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 3})
|
||||
org3 := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 3})
|
||||
user4 := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 4})
|
||||
|
||||
var issue1ID int64 = 1
|
||||
|
|
@ -144,7 +144,7 @@ func TestIssueCommentDeleteReaction(t *testing.T) {
|
|||
|
||||
addReaction(t, user1.ID, issue1ID, comment1ID, "heart")
|
||||
addReaction(t, user2.ID, issue1ID, comment1ID, "heart")
|
||||
addReaction(t, user3.ID, issue1ID, comment1ID, "heart")
|
||||
addReaction(t, org3.ID, issue1ID, comment1ID, "heart")
|
||||
addReaction(t, user4.ID, issue1ID, comment1ID, "+1")
|
||||
|
||||
reactionsList, _, err := issues_model.FindReactions(db.DefaultContext, issues_model.FindReactionsOptions{
|
||||
|
|
|
|||
|
|
@ -80,7 +80,7 @@ func TestFindLatestReviews(t *testing.T) {
|
|||
assert.NoError(t, err)
|
||||
assert.Len(t, reviews, 2)
|
||||
assert.Equal(t, "duplicate review from user5 (latest)", reviews[0].Content)
|
||||
assert.Equal(t, "singular review from user6 and final review for this pr", reviews[1].Content)
|
||||
assert.Equal(t, "singular review from org6 and final review for this pr", reviews[1].Content)
|
||||
}
|
||||
|
||||
func TestGetCurrentReview(t *testing.T) {
|
||||
|
|
@ -123,13 +123,13 @@ func TestGetReviewersByIssueID(t *testing.T) {
|
|||
|
||||
issue := unittest.AssertExistsAndLoadBean(t, &issues_model.Issue{ID: 3})
|
||||
user2 := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 2})
|
||||
user3 := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 3})
|
||||
org3 := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 3})
|
||||
user4 := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 4})
|
||||
|
||||
expectedReviews := []*issues_model.Review{}
|
||||
expectedReviews = append(expectedReviews,
|
||||
&issues_model.Review{
|
||||
Reviewer: user3,
|
||||
Reviewer: org3,
|
||||
Type: issues_model.ReviewTypeReject,
|
||||
UpdatedUnix: 946684812,
|
||||
},
|
||||
|
|
|
|||
|
|
@ -60,7 +60,7 @@ func TestCreateOrStopIssueStopwatch(t *testing.T) {
|
|||
|
||||
user2, err := user_model.GetUserByID(db.DefaultContext, 2)
|
||||
assert.NoError(t, err)
|
||||
user3, err := user_model.GetUserByID(db.DefaultContext, 3)
|
||||
org3, err := user_model.GetUserByID(db.DefaultContext, 3)
|
||||
assert.NoError(t, err)
|
||||
|
||||
issue1, err := issues_model.GetIssueByID(db.DefaultContext, 1)
|
||||
|
|
@ -68,7 +68,7 @@ func TestCreateOrStopIssueStopwatch(t *testing.T) {
|
|||
issue2, err := issues_model.GetIssueByID(db.DefaultContext, 2)
|
||||
assert.NoError(t, err)
|
||||
|
||||
assert.NoError(t, issues_model.CreateOrStopIssueStopwatch(user3, issue1))
|
||||
assert.NoError(t, issues_model.CreateOrStopIssueStopwatch(org3, issue1))
|
||||
sw := unittest.AssertExistsAndLoadBean(t, &issues_model.Stopwatch{UserID: 3, IssueID: 1})
|
||||
assert.LessOrEqual(t, sw.CreatedUnix, timeutil.TimeStampNow())
|
||||
|
||||
|
|
|
|||
|
|
@ -18,14 +18,14 @@ import (
|
|||
func TestAddTime(t *testing.T) {
|
||||
assert.NoError(t, unittest.PrepareTestDatabase())
|
||||
|
||||
user3, err := user_model.GetUserByID(db.DefaultContext, 3)
|
||||
org3, err := user_model.GetUserByID(db.DefaultContext, 3)
|
||||
assert.NoError(t, err)
|
||||
|
||||
issue1, err := issues_model.GetIssueByID(db.DefaultContext, 1)
|
||||
assert.NoError(t, err)
|
||||
|
||||
// 3661 = 1h 1min 1s
|
||||
trackedTime, err := issues_model.AddTime(db.DefaultContext, user3, issue1, 3661, time.Now())
|
||||
trackedTime, err := issues_model.AddTime(db.DefaultContext, org3, issue1, 3661, time.Now())
|
||||
assert.NoError(t, err)
|
||||
assert.Equal(t, int64(3), trackedTime.UserID)
|
||||
assert.Equal(t, int64(1), trackedTime.IssueID)
|
||||
|
|
|
|||
|
|
@ -115,10 +115,10 @@ func TestUser_GetMembers(t *testing.T) {
|
|||
func TestGetOrgByName(t *testing.T) {
|
||||
assert.NoError(t, unittest.PrepareTestDatabase())
|
||||
|
||||
org, err := organization.GetOrgByName(db.DefaultContext, "user3")
|
||||
org, err := organization.GetOrgByName(db.DefaultContext, "org3")
|
||||
assert.NoError(t, err)
|
||||
assert.EqualValues(t, 3, org.ID)
|
||||
assert.Equal(t, "user3", org.Name)
|
||||
assert.Equal(t, "org3", org.Name)
|
||||
|
||||
_, err = organization.GetOrgByName(db.DefaultContext, "user2") // user2 is an individual
|
||||
assert.True(t, organization.IsErrOrgNotExist(err))
|
||||
|
|
@ -343,7 +343,7 @@ func TestAccessibleReposEnv_MirrorRepos(t *testing.T) {
|
|||
func TestHasOrgVisibleTypePublic(t *testing.T) {
|
||||
assert.NoError(t, unittest.PrepareTestDatabase())
|
||||
owner := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 2})
|
||||
user3 := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 3})
|
||||
org3 := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 3})
|
||||
|
||||
const newOrgName = "test-org-public"
|
||||
org := &organization.Organization{
|
||||
|
|
@ -356,7 +356,7 @@ func TestHasOrgVisibleTypePublic(t *testing.T) {
|
|||
org = unittest.AssertExistsAndLoadBean(t,
|
||||
&organization.Organization{Name: org.Name, Type: user_model.UserTypeOrganization})
|
||||
test1 := organization.HasOrgOrUserVisible(db.DefaultContext, org.AsUser(), owner)
|
||||
test2 := organization.HasOrgOrUserVisible(db.DefaultContext, org.AsUser(), user3)
|
||||
test2 := organization.HasOrgOrUserVisible(db.DefaultContext, org.AsUser(), org3)
|
||||
test3 := organization.HasOrgOrUserVisible(db.DefaultContext, org.AsUser(), nil)
|
||||
assert.True(t, test1) // owner of org
|
||||
assert.True(t, test2) // user not a part of org
|
||||
|
|
@ -366,7 +366,7 @@ func TestHasOrgVisibleTypePublic(t *testing.T) {
|
|||
func TestHasOrgVisibleTypeLimited(t *testing.T) {
|
||||
assert.NoError(t, unittest.PrepareTestDatabase())
|
||||
owner := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 2})
|
||||
user3 := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 3})
|
||||
org3 := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 3})
|
||||
|
||||
const newOrgName = "test-org-limited"
|
||||
org := &organization.Organization{
|
||||
|
|
@ -379,7 +379,7 @@ func TestHasOrgVisibleTypeLimited(t *testing.T) {
|
|||
org = unittest.AssertExistsAndLoadBean(t,
|
||||
&organization.Organization{Name: org.Name, Type: user_model.UserTypeOrganization})
|
||||
test1 := organization.HasOrgOrUserVisible(db.DefaultContext, org.AsUser(), owner)
|
||||
test2 := organization.HasOrgOrUserVisible(db.DefaultContext, org.AsUser(), user3)
|
||||
test2 := organization.HasOrgOrUserVisible(db.DefaultContext, org.AsUser(), org3)
|
||||
test3 := organization.HasOrgOrUserVisible(db.DefaultContext, org.AsUser(), nil)
|
||||
assert.True(t, test1) // owner of org
|
||||
assert.True(t, test2) // user not a part of org
|
||||
|
|
@ -389,7 +389,7 @@ func TestHasOrgVisibleTypeLimited(t *testing.T) {
|
|||
func TestHasOrgVisibleTypePrivate(t *testing.T) {
|
||||
assert.NoError(t, unittest.PrepareTestDatabase())
|
||||
owner := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 2})
|
||||
user3 := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 3})
|
||||
org3 := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 3})
|
||||
|
||||
const newOrgName = "test-org-private"
|
||||
org := &organization.Organization{
|
||||
|
|
@ -402,7 +402,7 @@ func TestHasOrgVisibleTypePrivate(t *testing.T) {
|
|||
org = unittest.AssertExistsAndLoadBean(t,
|
||||
&organization.Organization{Name: org.Name, Type: user_model.UserTypeOrganization})
|
||||
test1 := organization.HasOrgOrUserVisible(db.DefaultContext, org.AsUser(), owner)
|
||||
test2 := organization.HasOrgOrUserVisible(db.DefaultContext, org.AsUser(), user3)
|
||||
test2 := organization.HasOrgOrUserVisible(db.DefaultContext, org.AsUser(), org3)
|
||||
test3 := organization.HasOrgOrUserVisible(db.DefaultContext, org.AsUser(), nil)
|
||||
assert.True(t, test1) // owner of org
|
||||
assert.False(t, test2) // user not a part of org
|
||||
|
|
@ -493,7 +493,7 @@ func TestCreateOrganization3(t *testing.T) {
|
|||
assert.NoError(t, unittest.PrepareTestDatabase())
|
||||
|
||||
owner := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 2})
|
||||
org := &organization.Organization{Name: "user3"} // should already exist
|
||||
org := &organization.Organization{Name: "org3"} // should already exist
|
||||
unittest.AssertExistsAndLoadBean(t, &user_model.User{Name: org.Name}) // sanity check
|
||||
err := organization.CreateOrganization(org, owner)
|
||||
assert.Error(t, err)
|
||||
|
|
|
|||
|
|
@ -30,12 +30,12 @@ func TestTeamInvite(t *testing.T) {
|
|||
t.Run("CreateAndRemove", func(t *testing.T) {
|
||||
user1 := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 1})
|
||||
|
||||
invite, err := organization.CreateTeamInvite(db.DefaultContext, user1, team, "user3@example.com")
|
||||
invite, err := organization.CreateTeamInvite(db.DefaultContext, user1, team, "org3@example.com")
|
||||
assert.NotNil(t, invite)
|
||||
assert.NoError(t, err)
|
||||
|
||||
// Shouldn't allow duplicate invite
|
||||
_, err = organization.CreateTeamInvite(db.DefaultContext, user1, team, "user3@example.com")
|
||||
_, err = organization.CreateTeamInvite(db.DefaultContext, user1, team, "org3@example.com")
|
||||
assert.Error(t, err)
|
||||
|
||||
// should remove invite
|
||||
|
|
|
|||
|
|
@ -66,7 +66,7 @@ func getTestCases() []struct {
|
|||
count: 0,
|
||||
},
|
||||
{
|
||||
name: "PublicRepositoriesOfUser3",
|
||||
name: "PublicRepositoriesOfOrg3",
|
||||
opts: &repo_model.SearchRepoOptions{ListOptions: db.ListOptions{Page: 1, PageSize: 10}, OwnerID: 20, Collaborate: util.OptionalBoolFalse},
|
||||
count: 2,
|
||||
},
|
||||
|
|
@ -81,7 +81,7 @@ func getTestCases() []struct {
|
|||
count: 0,
|
||||
},
|
||||
{
|
||||
name: "PublicAndPrivateRepositoriesOfUser3",
|
||||
name: "PublicAndPrivateRepositoriesOfOrg3",
|
||||
opts: &repo_model.SearchRepoOptions{ListOptions: db.ListOptions{Page: 1, PageSize: 10}, OwnerID: 20, Private: true, Collaborate: util.OptionalBoolFalse},
|
||||
count: 4,
|
||||
},
|
||||
|
|
@ -96,7 +96,7 @@ func getTestCases() []struct {
|
|||
count: 1,
|
||||
},
|
||||
{
|
||||
name: "PublicRepositoriesOfUser3IncludingCollaborative",
|
||||
name: "PublicRepositoriesOfOrg3IncludingCollaborative",
|
||||
opts: &repo_model.SearchRepoOptions{ListOptions: db.ListOptions{Page: 1, PageSize: 10}, OwnerID: 20},
|
||||
count: 3,
|
||||
},
|
||||
|
|
@ -111,7 +111,7 @@ func getTestCases() []struct {
|
|||
count: 4,
|
||||
},
|
||||
{
|
||||
name: "PublicAndPrivateRepositoriesOfUser3IncludingCollaborative",
|
||||
name: "PublicAndPrivateRepositoriesOfOrg3IncludingCollaborative",
|
||||
opts: &repo_model.SearchRepoOptions{ListOptions: db.ListOptions{Page: 1, PageSize: 10}, OwnerID: 20, Private: true},
|
||||
count: 7,
|
||||
},
|
||||
|
|
@ -168,7 +168,7 @@ func getTestCases() []struct {
|
|||
{
|
||||
name: "OwnerSlashRepoSearch",
|
||||
opts: &repo_model.SearchRepoOptions{Keyword: "user/repo2", ListOptions: db.ListOptions{Page: 1, PageSize: 10}, Private: true, OwnerID: 0},
|
||||
count: 3,
|
||||
count: 2,
|
||||
},
|
||||
{
|
||||
name: "OwnerSlashSearch",
|
||||
|
|
|
|||
|
|
@ -121,7 +121,7 @@ func TestMetas(t *testing.T) {
|
|||
metas = repo.ComposeMetas()
|
||||
assert.Contains(t, metas, "org")
|
||||
assert.Contains(t, metas, "teams")
|
||||
assert.Equal(t, "user3", metas["org"])
|
||||
assert.Equal(t, "org3", metas["org"])
|
||||
assert.Equal(t, ",owners,team1,", metas["teams"])
|
||||
}
|
||||
|
||||
|
|
|
|||
|
|
@ -41,10 +41,10 @@ func TestRepositoryTransfer(t *testing.T) {
|
|||
assert.NoError(t, transfer.LoadAttributes(db.DefaultContext))
|
||||
assert.Equal(t, "user2", transfer.Recipient.Name)
|
||||
|
||||
user6 := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 2})
|
||||
org6 := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 2})
|
||||
|
||||
// Only transfer can be started at any given time
|
||||
err = CreatePendingRepositoryTransfer(db.DefaultContext, doer, user6, repo.ID, nil)
|
||||
err = CreatePendingRepositoryTransfer(db.DefaultContext, doer, org6, repo.ID, nil)
|
||||
assert.Error(t, err)
|
||||
assert.True(t, IsErrRepoTransferInProgress(err))
|
||||
|
||||
|
|
|
|||
|
|
@ -209,7 +209,7 @@ func TestListEmails(t *testing.T) {
|
|||
}
|
||||
|
||||
assert.True(t, contains(func(s *user_model.SearchEmailResult) bool { return s.UID == 18 }))
|
||||
// 'user3' is an organization
|
||||
// 'org3' is an organization
|
||||
assert.False(t, contains(func(s *user_model.SearchEmailResult) bool { return s.UID == 3 }))
|
||||
|
||||
// Must find no records
|
||||
|
|
|
|||
|
|
@ -39,7 +39,7 @@ func TestGetUserEmailsByNames(t *testing.T) {
|
|||
assert.ElementsMatch(t, []string{"user8@example.com"}, user_model.GetUserEmailsByNames(db.DefaultContext, []string{"user8", "user9"}))
|
||||
assert.ElementsMatch(t, []string{"user8@example.com", "user5@example.com"}, user_model.GetUserEmailsByNames(db.DefaultContext, []string{"user8", "user5"}))
|
||||
|
||||
assert.ElementsMatch(t, []string{"user8@example.com"}, user_model.GetUserEmailsByNames(db.DefaultContext, []string{"user8", "user7"}))
|
||||
assert.ElementsMatch(t, []string{"user8@example.com"}, user_model.GetUserEmailsByNames(db.DefaultContext, []string{"user8", "org7"}))
|
||||
}
|
||||
|
||||
func TestCanCreateOrganization(t *testing.T) {
|
||||
|
|
@ -372,9 +372,9 @@ func TestUpdateUser(t *testing.T) {
|
|||
func TestUpdateUserEmailAlreadyUsed(t *testing.T) {
|
||||
assert.NoError(t, unittest.PrepareTestDatabase())
|
||||
user2 := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 2})
|
||||
user3 := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 3})
|
||||
org3 := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 3})
|
||||
|
||||
user2.Email = user3.Email
|
||||
user2.Email = org3.Email
|
||||
err := user_model.UpdateUser(db.DefaultContext, user2, true)
|
||||
assert.True(t, user_model.IsErrEmailAlreadyUsed(err))
|
||||
}
|
||||
|
|
|
|||
|
|
@ -78,15 +78,15 @@ func TestFindAllIssueReferences(t *testing.T) {
|
|||
[]testResult{},
|
||||
},
|
||||
{
|
||||
"This user3/repo4#200 yes.",
|
||||
"This org3/repo4#200 yes.",
|
||||
[]testResult{
|
||||
{200, "user3", "repo4", "200", false, XRefActionNone, &RefSpan{Start: 5, End: 20}, nil, ""},
|
||||
{200, "org3", "repo4", "200", false, XRefActionNone, &RefSpan{Start: 5, End: 19}, nil, ""},
|
||||
},
|
||||
},
|
||||
{
|
||||
"This user3/repo4!200 yes.",
|
||||
"This org3/repo4!200 yes.",
|
||||
[]testResult{
|
||||
{200, "user3", "repo4", "200", true, XRefActionNone, &RefSpan{Start: 5, End: 20}, nil, ""},
|
||||
{200, "org3", "repo4", "200", true, XRefActionNone, &RefSpan{Start: 5, End: 19}, nil, ""},
|
||||
},
|
||||
},
|
||||
{
|
||||
|
|
@ -106,13 +106,13 @@ func TestFindAllIssueReferences(t *testing.T) {
|
|||
},
|
||||
},
|
||||
{
|
||||
"This [four](http://gitea.com:3000/user3/repo4/issues/203) yes.",
|
||||
"This [four](http://gitea.com:3000/org3/repo4/issues/203) yes.",
|
||||
[]testResult{
|
||||
{203, "user3", "repo4", "203", false, XRefActionNone, nil, nil, ""},
|
||||
{203, "org3", "repo4", "203", false, XRefActionNone, nil, nil, ""},
|
||||
},
|
||||
},
|
||||
{
|
||||
"This [five](http://github.com/user3/repo4/issues/204) no.",
|
||||
"This [five](http://github.com/org3/repo4/issues/204) no.",
|
||||
[]testResult{},
|
||||
},
|
||||
{
|
||||
|
|
@ -151,9 +151,9 @@ func TestFindAllIssueReferences(t *testing.T) {
|
|||
},
|
||||
},
|
||||
{
|
||||
"Do you fix user6/repo6#300 ? yes",
|
||||
"Do you fix org6/repo6#300 ? yes",
|
||||
[]testResult{
|
||||
{300, "user6", "repo6", "300", false, XRefActionCloses, &RefSpan{Start: 11, End: 26}, &RefSpan{Start: 7, End: 10}, ""},
|
||||
{300, "org6", "repo6", "300", false, XRefActionCloses, &RefSpan{Start: 11, End: 25}, &RefSpan{Start: 7, End: 10}, ""},
|
||||
},
|
||||
},
|
||||
{
|
||||
|
|
@ -190,9 +190,9 @@ func TestFindAllIssueReferences(t *testing.T) {
|
|||
},
|
||||
},
|
||||
{
|
||||
"This user3/repo4#200, yes.",
|
||||
"This org3/repo4#200, yes.",
|
||||
[]testResult{
|
||||
{200, "user3", "repo4", "200", false, XRefActionNone, &RefSpan{Start: 5, End: 20}, nil, ""},
|
||||
{200, "org3", "repo4", "200", false, XRefActionNone, &RefSpan{Start: 5, End: 19}, nil, ""},
|
||||
},
|
||||
},
|
||||
{
|
||||
|
|
@ -498,15 +498,15 @@ func TestCustomizeCloseKeywords(t *testing.T) {
|
|||
},
|
||||
},
|
||||
{
|
||||
"Cerró user6/repo6#300 yes",
|
||||
"Cerró org6/repo6#300 yes",
|
||||
[]testResult{
|
||||
{300, "user6", "repo6", "300", false, XRefActionCloses, &RefSpan{Start: 7, End: 22}, &RefSpan{Start: 0, End: 6}, ""},
|
||||
{300, "org6", "repo6", "300", false, XRefActionCloses, &RefSpan{Start: 7, End: 21}, &RefSpan{Start: 0, End: 6}, ""},
|
||||
},
|
||||
},
|
||||
{
|
||||
"Reabre user3/repo4#200 yes",
|
||||
"Reabre org3/repo4#200 yes",
|
||||
[]testResult{
|
||||
{200, "user3", "repo4", "200", false, XRefActionReopens, &RefSpan{Start: 7, End: 22}, &RefSpan{Start: 0, End: 6}, ""},
|
||||
{200, "org3", "repo4", "200", false, XRefActionReopens, &RefSpan{Start: 7, End: 21}, &RefSpan{Start: 0, End: 6}, ""},
|
||||
},
|
||||
},
|
||||
}
|
||||
|
|
|
|||
|
|
@ -262,7 +262,7 @@ func TestUpdateIssuesCommit_AnotherRepoNoPermission(t *testing.T) {
|
|||
CommitterName: "User Ten",
|
||||
AuthorEmail: "user10@example.com",
|
||||
AuthorName: "User Ten",
|
||||
Message: "close user3/repo3#1",
|
||||
Message: "close org3/repo3#1",
|
||||
},
|
||||
{
|
||||
Sha1: "abcdef4",
|
||||
|
|
@ -270,7 +270,7 @@ func TestUpdateIssuesCommit_AnotherRepoNoPermission(t *testing.T) {
|
|||
CommitterName: "User Ten",
|
||||
AuthorEmail: "user10@example.com",
|
||||
AuthorName: "User Ten",
|
||||
Message: "close " + setting.AppURL + "user3/repo3/issues/1",
|
||||
Message: "close " + setting.AppURL + "org3/repo3/issues/1",
|
||||
},
|
||||
}
|
||||
|
||||
|
|
|
|||
|
|
@ -42,7 +42,7 @@ func TestTransferOwnership(t *testing.T) {
|
|||
transferredRepo := unittest.AssertExistsAndLoadBean(t, &repo_model.Repository{ID: 3})
|
||||
assert.EqualValues(t, 2, transferredRepo.OwnerID)
|
||||
|
||||
exist, err := util.IsExist(repo_model.RepoPath("user3", "repo3"))
|
||||
exist, err := util.IsExist(repo_model.RepoPath("org3", "repo3"))
|
||||
assert.NoError(t, err)
|
||||
assert.False(t, exist)
|
||||
exist, err = util.IsExist(repo_model.RepoPath("user2", "repo3"))
|
||||
|
|
@ -52,7 +52,7 @@ func TestTransferOwnership(t *testing.T) {
|
|||
OpType: activities_model.ActionTransferRepo,
|
||||
ActUserID: 2,
|
||||
RepoID: 3,
|
||||
Content: "user3/repo3",
|
||||
Content: "org3/repo3",
|
||||
})
|
||||
|
||||
unittest.CheckConsistencyFor(t, &repo_model.Repository{}, &user_model.User{}, &organization.Team{})
|
||||
|
|
|
|||
|
|
@ -28,7 +28,7 @@ import (
|
|||
func TestPullRequestTargetEvent(t *testing.T) {
|
||||
onGiteaRun(t, func(t *testing.T, u *url.URL) {
|
||||
user2 := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 2}) // owner of the base repo
|
||||
user3 := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 3}) // owner of the forked repo
|
||||
org3 := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 3}) // owner of the forked repo
|
||||
|
||||
// create the base repo
|
||||
baseRepo, err := repo_service.CreateRepository(db.DefaultContext, user2, user2, repo_service.CreateRepoOptions{
|
||||
|
|
@ -52,7 +52,7 @@ func TestPullRequestTargetEvent(t *testing.T) {
|
|||
assert.NoError(t, err)
|
||||
|
||||
// create the forked repo
|
||||
forkedRepo, err := repo_service.ForkRepository(git.DefaultContext, user2, user3, repo_service.ForkRepoOptions{
|
||||
forkedRepo, err := repo_service.ForkRepository(git.DefaultContext, user2, org3, repo_service.ForkRepoOptions{
|
||||
BaseRepo: baseRepo,
|
||||
Name: "forked-repo-pull-request-target",
|
||||
Description: "test pull-request-target event",
|
||||
|
|
@ -89,7 +89,7 @@ func TestPullRequestTargetEvent(t *testing.T) {
|
|||
assert.NotEmpty(t, addWorkflowToBaseResp)
|
||||
|
||||
// add a new file to the forked repo
|
||||
addFileToForkedResp, err := files_service.ChangeRepoFiles(git.DefaultContext, forkedRepo, user3, &files_service.ChangeRepoFilesOptions{
|
||||
addFileToForkedResp, err := files_service.ChangeRepoFiles(git.DefaultContext, forkedRepo, org3, &files_service.ChangeRepoFilesOptions{
|
||||
Files: []*files_service.ChangeRepoFile{
|
||||
{
|
||||
Operation: "create",
|
||||
|
|
@ -101,12 +101,12 @@ func TestPullRequestTargetEvent(t *testing.T) {
|
|||
OldBranch: "main",
|
||||
NewBranch: "fork-branch-1",
|
||||
Author: &files_service.IdentityOptions{
|
||||
Name: user3.Name,
|
||||
Email: user3.Email,
|
||||
Name: org3.Name,
|
||||
Email: org3.Email,
|
||||
},
|
||||
Committer: &files_service.IdentityOptions{
|
||||
Name: user3.Name,
|
||||
Email: user3.Email,
|
||||
Name: org3.Name,
|
||||
Email: org3.Email,
|
||||
},
|
||||
Dates: &files_service.CommitDateOptions{
|
||||
Author: time.Now(),
|
||||
|
|
@ -120,8 +120,8 @@ func TestPullRequestTargetEvent(t *testing.T) {
|
|||
pullIssue := &issues_model.Issue{
|
||||
RepoID: baseRepo.ID,
|
||||
Title: "Test pull-request-target-event",
|
||||
PosterID: user3.ID,
|
||||
Poster: user3,
|
||||
PosterID: org3.ID,
|
||||
Poster: org3,
|
||||
IsPull: true,
|
||||
}
|
||||
pullRequest := &issues_model.PullRequest{
|
||||
|
|
@ -143,7 +143,7 @@ func TestPullRequestTargetEvent(t *testing.T) {
|
|||
assert.Equal(t, actions_module.GithubEventPullRequestTarget, actionRun.TriggerEvent)
|
||||
|
||||
// add another file whose name cannot match the specified path
|
||||
addFileToForkedResp, err = files_service.ChangeRepoFiles(git.DefaultContext, forkedRepo, user3, &files_service.ChangeRepoFilesOptions{
|
||||
addFileToForkedResp, err = files_service.ChangeRepoFiles(git.DefaultContext, forkedRepo, org3, &files_service.ChangeRepoFilesOptions{
|
||||
Files: []*files_service.ChangeRepoFile{
|
||||
{
|
||||
Operation: "create",
|
||||
|
|
@ -155,12 +155,12 @@ func TestPullRequestTargetEvent(t *testing.T) {
|
|||
OldBranch: "main",
|
||||
NewBranch: "fork-branch-2",
|
||||
Author: &files_service.IdentityOptions{
|
||||
Name: user3.Name,
|
||||
Email: user3.Email,
|
||||
Name: org3.Name,
|
||||
Email: org3.Email,
|
||||
},
|
||||
Committer: &files_service.IdentityOptions{
|
||||
Name: user3.Name,
|
||||
Email: user3.Email,
|
||||
Name: org3.Name,
|
||||
Email: org3.Email,
|
||||
},
|
||||
Dates: &files_service.CommitDateOptions{
|
||||
Author: time.Now(),
|
||||
|
|
@ -174,8 +174,8 @@ func TestPullRequestTargetEvent(t *testing.T) {
|
|||
pullIssue = &issues_model.Issue{
|
||||
RepoID: baseRepo.ID,
|
||||
Title: "A mismatched path cannot trigger pull-request-target-event",
|
||||
PosterID: user3.ID,
|
||||
Poster: user3,
|
||||
PosterID: org3.ID,
|
||||
Poster: org3,
|
||||
IsPull: true,
|
||||
}
|
||||
pullRequest = &issues_model.PullRequest{
|
||||
|
|
|
|||
|
|
@ -298,14 +298,14 @@ func TestAPISearchIssues(t *testing.T) {
|
|||
DecodeJSON(t, resp, &apiIssues)
|
||||
assert.Len(t, apiIssues, 8)
|
||||
|
||||
query = url.Values{"owner": {"user3"}, "token": {token}} // organization
|
||||
query = url.Values{"owner": {"org3"}, "token": {token}} // organization
|
||||
link.RawQuery = query.Encode()
|
||||
req = NewRequest(t, "GET", link.String())
|
||||
resp = MakeRequest(t, req, http.StatusOK)
|
||||
DecodeJSON(t, resp, &apiIssues)
|
||||
assert.Len(t, apiIssues, 5)
|
||||
|
||||
query = url.Values{"owner": {"user3"}, "team": {"team1"}, "token": {token}} // organization + team
|
||||
query = url.Values{"owner": {"org3"}, "team": {"team1"}, "token": {token}} // organization + team
|
||||
link.RawQuery = query.Encode()
|
||||
req = NewRequest(t, "GET", link.String())
|
||||
resp = MakeRequest(t, req, http.StatusOK)
|
||||
|
|
|
|||
|
|
@ -34,7 +34,7 @@ func TestAPIUpdateOrgAvatar(t *testing.T) {
|
|||
Image: base64.StdEncoding.EncodeToString(avatar),
|
||||
}
|
||||
|
||||
req := NewRequestWithJSON(t, "POST", "/api/v1/orgs/user3/avatar?token="+token, &opts)
|
||||
req := NewRequestWithJSON(t, "POST", "/api/v1/orgs/org3/avatar?token="+token, &opts)
|
||||
MakeRequest(t, req, http.StatusNoContent)
|
||||
|
||||
// Test what happens if you don't have a valid Base64 string
|
||||
|
|
@ -42,7 +42,7 @@ func TestAPIUpdateOrgAvatar(t *testing.T) {
|
|||
Image: "Invalid",
|
||||
}
|
||||
|
||||
req = NewRequestWithJSON(t, "POST", "/api/v1/orgs/user3/avatar?token="+token, &opts)
|
||||
req = NewRequestWithJSON(t, "POST", "/api/v1/orgs/org3/avatar?token="+token, &opts)
|
||||
MakeRequest(t, req, http.StatusBadRequest)
|
||||
|
||||
// Test what happens if you use a file that is not an image
|
||||
|
|
@ -56,7 +56,7 @@ func TestAPIUpdateOrgAvatar(t *testing.T) {
|
|||
Image: base64.StdEncoding.EncodeToString(text),
|
||||
}
|
||||
|
||||
req = NewRequestWithJSON(t, "POST", "/api/v1/orgs/user3/avatar?token="+token, &opts)
|
||||
req = NewRequestWithJSON(t, "POST", "/api/v1/orgs/org3/avatar?token="+token, &opts)
|
||||
MakeRequest(t, req, http.StatusInternalServerError)
|
||||
}
|
||||
|
||||
|
|
@ -67,6 +67,6 @@ func TestAPIDeleteOrgAvatar(t *testing.T) {
|
|||
|
||||
token := getTokenForLoggedInUser(t, session, auth_model.AccessTokenScopeWriteOrganization)
|
||||
|
||||
req := NewRequest(t, "DELETE", "/api/v1/orgs/user3/avatar?token="+token)
|
||||
req := NewRequest(t, "DELETE", "/api/v1/orgs/org3/avatar?token="+token)
|
||||
MakeRequest(t, req, http.StatusNoContent)
|
||||
}
|
||||
|
|
|
|||
|
|
@ -102,19 +102,19 @@ func TestAPIOrgEdit(t *testing.T) {
|
|||
|
||||
token := getTokenForLoggedInUser(t, session, auth_model.AccessTokenScopeWriteOrganization)
|
||||
org := api.EditOrgOption{
|
||||
FullName: "User3 organization new full name",
|
||||
FullName: "Org3 organization new full name",
|
||||
Description: "A new description",
|
||||
Website: "https://try.gitea.io/new",
|
||||
Location: "Beijing",
|
||||
Visibility: "private",
|
||||
}
|
||||
req := NewRequestWithJSON(t, "PATCH", "/api/v1/orgs/user3?token="+token, &org)
|
||||
req := NewRequestWithJSON(t, "PATCH", "/api/v1/orgs/org3?token="+token, &org)
|
||||
resp := MakeRequest(t, req, http.StatusOK)
|
||||
|
||||
var apiOrg api.Organization
|
||||
DecodeJSON(t, resp, &apiOrg)
|
||||
|
||||
assert.Equal(t, "user3", apiOrg.Name)
|
||||
assert.Equal(t, "org3", apiOrg.Name)
|
||||
assert.Equal(t, org.FullName, apiOrg.FullName)
|
||||
assert.Equal(t, org.Description, apiOrg.Description)
|
||||
assert.Equal(t, org.Website, apiOrg.Website)
|
||||
|
|
@ -129,13 +129,13 @@ func TestAPIOrgEditBadVisibility(t *testing.T) {
|
|||
|
||||
token := getTokenForLoggedInUser(t, session, auth_model.AccessTokenScopeWriteOrganization)
|
||||
org := api.EditOrgOption{
|
||||
FullName: "User3 organization new full name",
|
||||
FullName: "Org3 organization new full name",
|
||||
Description: "A new description",
|
||||
Website: "https://try.gitea.io/new",
|
||||
Location: "Beijing",
|
||||
Visibility: "badvisibility",
|
||||
}
|
||||
req := NewRequestWithJSON(t, "PATCH", "/api/v1/orgs/user3?token="+token, &org)
|
||||
req := NewRequestWithJSON(t, "PATCH", "/api/v1/orgs/org3?token="+token, &org)
|
||||
MakeRequest(t, req, http.StatusUnprocessableEntity)
|
||||
})
|
||||
}
|
||||
|
|
@ -180,7 +180,7 @@ func TestAPIGetAll(t *testing.T) {
|
|||
|
||||
DecodeJSON(t, resp, &apiOrgList)
|
||||
assert.Len(t, apiOrgList, 7)
|
||||
assert.Equal(t, "org25", apiOrgList[0].FullName)
|
||||
assert.Equal(t, "org 17", apiOrgList[0].FullName)
|
||||
assert.Equal(t, "public", apiOrgList[0].Visibility)
|
||||
}
|
||||
|
||||
|
|
|
|||
|
|
@ -30,7 +30,7 @@ func TestAPIRepoBranchesPlain(t *testing.T) {
|
|||
session := loginUser(t, user1.LowerName)
|
||||
token := getTokenForLoggedInUser(t, session, auth_model.AccessTokenScopeWriteRepository)
|
||||
|
||||
link, _ := url.Parse(fmt.Sprintf("/api/v1/repos/user3/%s/branches", repo3.Name)) // a plain repo
|
||||
link, _ := url.Parse(fmt.Sprintf("/api/v1/repos/org3/%s/branches", repo3.Name)) // a plain repo
|
||||
link.RawQuery = url.Values{"token": {token}}.Encode()
|
||||
resp := MakeRequest(t, NewRequest(t, "GET", link.String()), http.StatusOK)
|
||||
bs, err := io.ReadAll(resp.Body)
|
||||
|
|
@ -42,7 +42,7 @@ func TestAPIRepoBranchesPlain(t *testing.T) {
|
|||
assert.EqualValues(t, "test_branch", branches[0].Name)
|
||||
assert.EqualValues(t, "master", branches[1].Name)
|
||||
|
||||
link2, _ := url.Parse(fmt.Sprintf("/api/v1/repos/user3/%s/branches/test_branch", repo3.Name))
|
||||
link2, _ := url.Parse(fmt.Sprintf("/api/v1/repos/org3/%s/branches/test_branch", repo3.Name))
|
||||
link2.RawQuery = url.Values{"token": {token}}.Encode()
|
||||
resp = MakeRequest(t, NewRequest(t, "GET", link2.String()), http.StatusOK)
|
||||
bs, err = io.ReadAll(resp.Body)
|
||||
|
|
@ -73,7 +73,7 @@ func TestAPIRepoBranchesPlain(t *testing.T) {
|
|||
assert.EqualValues(t, "test_branch2", branches[1].Name)
|
||||
assert.EqualValues(t, "master", branches[2].Name)
|
||||
|
||||
link3, _ := url.Parse(fmt.Sprintf("/api/v1/repos/user3/%s/branches/test_branch2", repo3.Name))
|
||||
link3, _ := url.Parse(fmt.Sprintf("/api/v1/repos/org3/%s/branches/test_branch2", repo3.Name))
|
||||
MakeRequest(t, NewRequest(t, "DELETE", link3.String()), http.StatusNotFound)
|
||||
|
||||
link3.RawQuery = url.Values{"token": {token}}.Encode()
|
||||
|
|
@ -90,7 +90,7 @@ func TestAPIRepoBranchesMirror(t *testing.T) {
|
|||
session := loginUser(t, user1.LowerName)
|
||||
token := getTokenForLoggedInUser(t, session, auth_model.AccessTokenScopeWriteRepository)
|
||||
|
||||
link, _ := url.Parse(fmt.Sprintf("/api/v1/repos/user3/%s/branches", repo5.Name)) // a mirror repo
|
||||
link, _ := url.Parse(fmt.Sprintf("/api/v1/repos/org3/%s/branches", repo5.Name)) // a mirror repo
|
||||
link.RawQuery = url.Values{"token": {token}}.Encode()
|
||||
resp := MakeRequest(t, NewRequest(t, "GET", link.String()), http.StatusOK)
|
||||
bs, err := io.ReadAll(resp.Body)
|
||||
|
|
@ -102,7 +102,7 @@ func TestAPIRepoBranchesMirror(t *testing.T) {
|
|||
assert.EqualValues(t, "test_branch", branches[0].Name)
|
||||
assert.EqualValues(t, "master", branches[1].Name)
|
||||
|
||||
link2, _ := url.Parse(fmt.Sprintf("/api/v1/repos/user3/%s/branches/test_branch", repo5.Name))
|
||||
link2, _ := url.Parse(fmt.Sprintf("/api/v1/repos/org3/%s/branches/test_branch", repo5.Name))
|
||||
link2.RawQuery = url.Values{"token": {token}}.Encode()
|
||||
resp = MakeRequest(t, NewRequest(t, "GET", link2.String()), http.StatusOK)
|
||||
bs, err = io.ReadAll(resp.Body)
|
||||
|
|
|
|||
|
|
@ -138,7 +138,7 @@ func TestAPIRepoEdit(t *testing.T) {
|
|||
bFalse, bTrue := false, true
|
||||
|
||||
user2 := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 2}) // owner of the repo1 & repo16
|
||||
user3 := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 3}) // owner of the repo3, is an org
|
||||
org3 := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 3}) // owner of the repo3, is an org
|
||||
user4 := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 4}) // owner of neither repos
|
||||
repo1 := unittest.AssertExistsAndLoadBean(t, &repo_model.Repository{ID: 1}) // public repo
|
||||
repo3 := unittest.AssertExistsAndLoadBean(t, &repo_model.Repository{ID: 3}) // public repo
|
||||
|
|
@ -330,21 +330,21 @@ func TestAPIRepoEdit(t *testing.T) {
|
|||
})
|
||||
_ = MakeRequest(t, req, http.StatusOK)
|
||||
|
||||
// Test using org repo "user3/repo3" where user2 is a collaborator
|
||||
// Test using org repo "org3/repo3" where user2 is a collaborator
|
||||
origRepoEditOption = getRepoEditOptionFromRepo(repo3)
|
||||
repoEditOption = getNewRepoEditOption(origRepoEditOption)
|
||||
url = fmt.Sprintf("/api/v1/repos/%s/%s?token=%s", user3.Name, repo3.Name, token2)
|
||||
url = fmt.Sprintf("/api/v1/repos/%s/%s?token=%s", org3.Name, repo3.Name, token2)
|
||||
req = NewRequestWithJSON(t, "PATCH", url, &repoEditOption)
|
||||
MakeRequest(t, req, http.StatusOK)
|
||||
// reset repo in db
|
||||
url = fmt.Sprintf("/api/v1/repos/%s/%s?token=%s", user3.Name, *repoEditOption.Name, token2)
|
||||
url = fmt.Sprintf("/api/v1/repos/%s/%s?token=%s", org3.Name, *repoEditOption.Name, token2)
|
||||
req = NewRequestWithJSON(t, "PATCH", url, &origRepoEditOption)
|
||||
_ = MakeRequest(t, req, http.StatusOK)
|
||||
|
||||
// Test using org repo "user3/repo3" with no user token
|
||||
// Test using org repo "org3/repo3" with no user token
|
||||
origRepoEditOption = getRepoEditOptionFromRepo(repo3)
|
||||
repoEditOption = getNewRepoEditOption(origRepoEditOption)
|
||||
url = fmt.Sprintf("/api/v1/repos/%s/%s", user3.Name, repo3.Name)
|
||||
url = fmt.Sprintf("/api/v1/repos/%s/%s", org3.Name, repo3.Name)
|
||||
req = NewRequestWithJSON(t, "PATCH", url, &repoEditOption)
|
||||
MakeRequest(t, req, http.StatusNotFound)
|
||||
|
||||
|
|
|
|||
|
|
@ -141,7 +141,7 @@ func BenchmarkAPICreateFileMedium(b *testing.B) {
|
|||
func TestAPICreateFile(t *testing.T) {
|
||||
onGiteaRun(t, func(t *testing.T, u *url.URL) {
|
||||
user2 := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 2}) // owner of the repo1 & repo16
|
||||
user3 := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 3}) // owner of the repo3, is an org
|
||||
org3 := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 3}) // owner of the repo3, is an org
|
||||
user4 := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 4}) // owner of neither repos
|
||||
repo1 := unittest.AssertExistsAndLoadBean(t, &repo_model.Repository{ID: 1}) // public repo
|
||||
repo3 := unittest.AssertExistsAndLoadBean(t, &repo_model.Repository{ID: 3}) // public repo
|
||||
|
|
@ -254,19 +254,19 @@ func TestAPICreateFile(t *testing.T) {
|
|||
req = NewRequestWithJSON(t, "POST", url, &createFileOptions)
|
||||
MakeRequest(t, req, http.StatusCreated)
|
||||
|
||||
// Test using org repo "user3/repo3" where user2 is a collaborator
|
||||
// Test using org repo "org3/repo3" where user2 is a collaborator
|
||||
createFileOptions = getCreateFileOptions()
|
||||
fileID++
|
||||
treePath = fmt.Sprintf("new/file%d.txt", fileID)
|
||||
url = fmt.Sprintf("/api/v1/repos/%s/%s/contents/%s?token=%s", user3.Name, repo3.Name, treePath, token2)
|
||||
url = fmt.Sprintf("/api/v1/repos/%s/%s/contents/%s?token=%s", org3.Name, repo3.Name, treePath, token2)
|
||||
req = NewRequestWithJSON(t, "POST", url, &createFileOptions)
|
||||
MakeRequest(t, req, http.StatusCreated)
|
||||
|
||||
// Test using org repo "user3/repo3" with no user token
|
||||
// Test using org repo "org3/repo3" with no user token
|
||||
createFileOptions = getCreateFileOptions()
|
||||
fileID++
|
||||
treePath = fmt.Sprintf("new/file%d.txt", fileID)
|
||||
url = fmt.Sprintf("/api/v1/repos/%s/%s/contents/%s", user3.Name, repo3.Name, treePath)
|
||||
url = fmt.Sprintf("/api/v1/repos/%s/%s/contents/%s", org3.Name, repo3.Name, treePath)
|
||||
req = NewRequestWithJSON(t, "POST", url, &createFileOptions)
|
||||
MakeRequest(t, req, http.StatusNotFound)
|
||||
|
||||
|
|
|
|||
|
|
@ -40,7 +40,7 @@ func getDeleteFileOptions() *api.DeleteFileOptions {
|
|||
func TestAPIDeleteFile(t *testing.T) {
|
||||
onGiteaRun(t, func(t *testing.T, u *url.URL) {
|
||||
user2 := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 2}) // owner of the repo1 & repo16
|
||||
user3 := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 3}) // owner of the repo3, is an org
|
||||
org3 := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 3}) // owner of the repo3, is an org
|
||||
user4 := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 4}) // owner of neither repos
|
||||
repo1 := unittest.AssertExistsAndLoadBean(t, &repo_model.Repository{ID: 1}) // public repo
|
||||
repo3 := unittest.AssertExistsAndLoadBean(t, &repo_model.Repository{ID: 3}) // public repo
|
||||
|
|
@ -139,21 +139,21 @@ func TestAPIDeleteFile(t *testing.T) {
|
|||
req = NewRequestWithJSON(t, "DELETE", url, &deleteFileOptions)
|
||||
MakeRequest(t, req, http.StatusOK)
|
||||
|
||||
// Test using org repo "user3/repo3" where user2 is a collaborator
|
||||
// Test using org repo "org3/repo3" where user2 is a collaborator
|
||||
fileID++
|
||||
treePath = fmt.Sprintf("delete/file%d.txt", fileID)
|
||||
createFile(user3, repo3, treePath)
|
||||
createFile(org3, repo3, treePath)
|
||||
deleteFileOptions = getDeleteFileOptions()
|
||||
url = fmt.Sprintf("/api/v1/repos/%s/%s/contents/%s?token=%s", user3.Name, repo3.Name, treePath, token2)
|
||||
url = fmt.Sprintf("/api/v1/repos/%s/%s/contents/%s?token=%s", org3.Name, repo3.Name, treePath, token2)
|
||||
req = NewRequestWithJSON(t, "DELETE", url, &deleteFileOptions)
|
||||
MakeRequest(t, req, http.StatusOK)
|
||||
|
||||
// Test using org repo "user3/repo3" with no user token
|
||||
// Test using org repo "org3/repo3" with no user token
|
||||
fileID++
|
||||
treePath = fmt.Sprintf("delete/file%d.txt", fileID)
|
||||
createFile(user3, repo3, treePath)
|
||||
createFile(org3, repo3, treePath)
|
||||
deleteFileOptions = getDeleteFileOptions()
|
||||
url = fmt.Sprintf("/api/v1/repos/%s/%s/contents/%s", user3.Name, repo3.Name, treePath)
|
||||
url = fmt.Sprintf("/api/v1/repos/%s/%s/contents/%s", org3.Name, repo3.Name, treePath)
|
||||
req = NewRequestWithJSON(t, "DELETE", url, &deleteFileOptions)
|
||||
MakeRequest(t, req, http.StatusNotFound)
|
||||
|
||||
|
|
|
|||
|
|
@ -108,7 +108,7 @@ func getExpectedFileResponseForUpdate(commitID, treePath, lastCommitSHA string)
|
|||
func TestAPIUpdateFile(t *testing.T) {
|
||||
onGiteaRun(t, func(t *testing.T, u *url.URL) {
|
||||
user2 := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 2}) // owner of the repo1 & repo16
|
||||
user3 := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 3}) // owner of the repo3, is an org
|
||||
org3 := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 3}) // owner of the repo3, is an org
|
||||
user4 := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 4}) // owner of neither repos
|
||||
repo1 := unittest.AssertExistsAndLoadBean(t, &repo_model.Repository{ID: 1}) // public repo
|
||||
repo3 := unittest.AssertExistsAndLoadBean(t, &repo_model.Repository{ID: 3}) // public repo
|
||||
|
|
@ -247,21 +247,21 @@ func TestAPIUpdateFile(t *testing.T) {
|
|||
req = NewRequestWithJSON(t, "PUT", url, &updateFileOptions)
|
||||
MakeRequest(t, req, http.StatusOK)
|
||||
|
||||
// Test using org repo "user3/repo3" where user2 is a collaborator
|
||||
// Test using org repo "org3/repo3" where user2 is a collaborator
|
||||
fileID++
|
||||
treePath = fmt.Sprintf("update/file%d.txt", fileID)
|
||||
createFile(user3, repo3, treePath)
|
||||
createFile(org3, repo3, treePath)
|
||||
updateFileOptions = getUpdateFileOptions()
|
||||
url = fmt.Sprintf("/api/v1/repos/%s/%s/contents/%s?token=%s", user3.Name, repo3.Name, treePath, token2)
|
||||
url = fmt.Sprintf("/api/v1/repos/%s/%s/contents/%s?token=%s", org3.Name, repo3.Name, treePath, token2)
|
||||
req = NewRequestWithJSON(t, "PUT", url, &updateFileOptions)
|
||||
MakeRequest(t, req, http.StatusOK)
|
||||
|
||||
// Test using org repo "user3/repo3" with no user token
|
||||
// Test using org repo "org3/repo3" with no user token
|
||||
fileID++
|
||||
treePath = fmt.Sprintf("update/file%d.txt", fileID)
|
||||
createFile(user3, repo3, treePath)
|
||||
createFile(org3, repo3, treePath)
|
||||
updateFileOptions = getUpdateFileOptions()
|
||||
url = fmt.Sprintf("/api/v1/repos/%s/%s/contents/%s", user3.Name, repo3.Name, treePath)
|
||||
url = fmt.Sprintf("/api/v1/repos/%s/%s/contents/%s", org3.Name, repo3.Name, treePath)
|
||||
req = NewRequestWithJSON(t, "PUT", url, &updateFileOptions)
|
||||
MakeRequest(t, req, http.StatusNotFound)
|
||||
|
||||
|
|
|
|||
|
|
@ -63,7 +63,7 @@ func getChangeFilesOptions() *api.ChangeFilesOptions {
|
|||
func TestAPIChangeFiles(t *testing.T) {
|
||||
onGiteaRun(t, func(t *testing.T, u *url.URL) {
|
||||
user2 := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 2}) // owner of the repo1 & repo16
|
||||
user3 := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 3}) // owner of the repo3, is an org
|
||||
org3 := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 3}) // owner of the repo3, is an org
|
||||
user4 := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 4}) // owner of neither repos
|
||||
repo1 := unittest.AssertExistsAndLoadBean(t, &repo_model.Repository{ID: 1}) // public repo
|
||||
repo3 := unittest.AssertExistsAndLoadBean(t, &repo_model.Repository{ID: 3}) // public repo
|
||||
|
|
@ -261,33 +261,33 @@ func TestAPIChangeFiles(t *testing.T) {
|
|||
req = NewRequestWithJSON(t, "POST", url, &changeFilesOptions)
|
||||
MakeRequest(t, req, http.StatusCreated)
|
||||
|
||||
// Test using org repo "user3/repo3" where user2 is a collaborator
|
||||
// Test using org repo "org3/repo3" where user2 is a collaborator
|
||||
fileID++
|
||||
createTreePath = fmt.Sprintf("new/file%d.txt", fileID)
|
||||
updateTreePath = fmt.Sprintf("update/file%d.txt", fileID)
|
||||
deleteTreePath = fmt.Sprintf("delete/file%d.txt", fileID)
|
||||
createFile(user3, repo3, updateTreePath)
|
||||
createFile(user3, repo3, deleteTreePath)
|
||||
createFile(org3, repo3, updateTreePath)
|
||||
createFile(org3, repo3, deleteTreePath)
|
||||
changeFilesOptions = getChangeFilesOptions()
|
||||
changeFilesOptions.Files[0].Path = createTreePath
|
||||
changeFilesOptions.Files[1].Path = updateTreePath
|
||||
changeFilesOptions.Files[2].Path = deleteTreePath
|
||||
url = fmt.Sprintf("/api/v1/repos/%s/%s/contents?token=%s", user3.Name, repo3.Name, token2)
|
||||
url = fmt.Sprintf("/api/v1/repos/%s/%s/contents?token=%s", org3.Name, repo3.Name, token2)
|
||||
req = NewRequestWithJSON(t, "POST", url, &changeFilesOptions)
|
||||
MakeRequest(t, req, http.StatusCreated)
|
||||
|
||||
// Test using org repo "user3/repo3" with no user token
|
||||
// Test using org repo "org3/repo3" with no user token
|
||||
fileID++
|
||||
createTreePath = fmt.Sprintf("new/file%d.txt", fileID)
|
||||
updateTreePath = fmt.Sprintf("update/file%d.txt", fileID)
|
||||
deleteTreePath = fmt.Sprintf("delete/file%d.txt", fileID)
|
||||
createFile(user3, repo3, updateTreePath)
|
||||
createFile(user3, repo3, deleteTreePath)
|
||||
createFile(org3, repo3, updateTreePath)
|
||||
createFile(org3, repo3, deleteTreePath)
|
||||
changeFilesOptions = getChangeFilesOptions()
|
||||
changeFilesOptions.Files[0].Path = createTreePath
|
||||
changeFilesOptions.Files[1].Path = updateTreePath
|
||||
changeFilesOptions.Files[2].Path = deleteTreePath
|
||||
url = fmt.Sprintf("/api/v1/repos/%s/%s/contents", user3.Name, repo3.Name)
|
||||
url = fmt.Sprintf("/api/v1/repos/%s/%s/contents", org3.Name, repo3.Name)
|
||||
req = NewRequestWithJSON(t, "POST", url, &changeFilesOptions)
|
||||
MakeRequest(t, req, http.StatusNotFound)
|
||||
|
||||
|
|
|
|||
|
|
@ -56,7 +56,7 @@ func TestAPIGetContentsList(t *testing.T) {
|
|||
func testAPIGetContentsList(t *testing.T, u *url.URL) {
|
||||
/*** SETUP ***/
|
||||
user2 := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 2}) // owner of the repo1 & repo16
|
||||
user3 := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 3}) // owner of the repo3, is an org
|
||||
org3 := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 3}) // owner of the repo3, is an org
|
||||
user4 := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 4}) // owner of neither repos
|
||||
repo1 := unittest.AssertExistsAndLoadBean(t, &repo_model.Repository{ID: 1}) // public repo
|
||||
repo3 := unittest.AssertExistsAndLoadBean(t, &repo_model.Repository{ID: 3}) // public repo
|
||||
|
|
@ -160,7 +160,7 @@ func testAPIGetContentsList(t *testing.T, u *url.URL) {
|
|||
req = NewRequestf(t, "GET", "/api/v1/repos/%s/%s/contents/readme.md?token=%s", user2.Name, repo16.Name, token2)
|
||||
MakeRequest(t, req, http.StatusOK)
|
||||
|
||||
// Test access of org user3 private repo file by owner user2
|
||||
req = NewRequestf(t, "GET", "/api/v1/repos/%s/%s/contents/%s?token=%s", user3.Name, repo3.Name, treePath, token2)
|
||||
// Test access of org org3 private repo file by owner user2
|
||||
req = NewRequestf(t, "GET", "/api/v1/repos/%s/%s/contents/%s?token=%s", org3.Name, repo3.Name, treePath, token2)
|
||||
MakeRequest(t, req, http.StatusOK)
|
||||
}
|
||||
|
|
|
|||
|
|
@ -58,7 +58,7 @@ func TestAPIGetContents(t *testing.T) {
|
|||
func testAPIGetContents(t *testing.T, u *url.URL) {
|
||||
/*** SETUP ***/
|
||||
user2 := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 2}) // owner of the repo1 & repo16
|
||||
user3 := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 3}) // owner of the repo3, is an org
|
||||
org3 := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 3}) // owner of the repo3, is an org
|
||||
user4 := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 4}) // owner of neither repos
|
||||
repo1 := unittest.AssertExistsAndLoadBean(t, &repo_model.Repository{ID: 1}) // public repo
|
||||
repo3 := unittest.AssertExistsAndLoadBean(t, &repo_model.Repository{ID: 3}) // public repo
|
||||
|
|
@ -157,8 +157,8 @@ func testAPIGetContents(t *testing.T, u *url.URL) {
|
|||
req = NewRequestf(t, "GET", "/api/v1/repos/%s/%s/contents/readme.md?token=%s", user2.Name, repo16.Name, token2)
|
||||
MakeRequest(t, req, http.StatusOK)
|
||||
|
||||
// Test access of org user3 private repo file by owner user2
|
||||
req = NewRequestf(t, "GET", "/api/v1/repos/%s/%s/contents/%s?token=%s", user3.Name, repo3.Name, treePath, token2)
|
||||
// Test access of org org3 private repo file by owner user2
|
||||
req = NewRequestf(t, "GET", "/api/v1/repos/%s/%s/contents/%s?token=%s", org3.Name, repo3.Name, treePath, token2)
|
||||
MakeRequest(t, req, http.StatusOK)
|
||||
}
|
||||
|
||||
|
|
|
|||
|
|
@ -20,7 +20,7 @@ import (
|
|||
func TestAPIReposGitBlobs(t *testing.T) {
|
||||
defer tests.PrepareTestEnv(t)()
|
||||
user2 := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 2}) // owner of the repo1 & repo16
|
||||
user3 := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 3}) // owner of the repo3
|
||||
org3 := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 3}) // owner of the repo3
|
||||
user4 := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 4}) // owner of neither repos
|
||||
repo1 := unittest.AssertExistsAndLoadBean(t, &repo_model.Repository{ID: 1}) // public repo
|
||||
repo3 := unittest.AssertExistsAndLoadBean(t, &repo_model.Repository{ID: 3}) // public repo
|
||||
|
|
@ -55,23 +55,23 @@ func TestAPIReposGitBlobs(t *testing.T) {
|
|||
req = NewRequestf(t, "GET", "/api/v1/repos/%s/%s/git/blobs/%s", user2.Name, repo1.Name, badSHA)
|
||||
MakeRequest(t, req, http.StatusBadRequest)
|
||||
|
||||
// Test using org repo "user3/repo3" where user2 is a collaborator
|
||||
req = NewRequestf(t, "GET", "/api/v1/repos/%s/%s/git/blobs/%s?token=%s", user3.Name, repo3.Name, repo3ReadmeSHA, token)
|
||||
// Test using org repo "org3/repo3" where user2 is a collaborator
|
||||
req = NewRequestf(t, "GET", "/api/v1/repos/%s/%s/git/blobs/%s?token=%s", org3.Name, repo3.Name, repo3ReadmeSHA, token)
|
||||
MakeRequest(t, req, http.StatusOK)
|
||||
|
||||
// Test using org repo "user3/repo3" where user2 is a collaborator
|
||||
req = NewRequestf(t, "GET", "/api/v1/repos/%s/%s/git/blobs/%s?token=%s", user3.Name, repo3.Name, repo3ReadmeSHA, token)
|
||||
// Test using org repo "org3/repo3" where user2 is a collaborator
|
||||
req = NewRequestf(t, "GET", "/api/v1/repos/%s/%s/git/blobs/%s?token=%s", org3.Name, repo3.Name, repo3ReadmeSHA, token)
|
||||
MakeRequest(t, req, http.StatusOK)
|
||||
|
||||
// Test using org repo "user3/repo3" with no user token
|
||||
req = NewRequestf(t, "GET", "/api/v1/repos/%s/%s/git/blobs/%s", user3.Name, repo3ReadmeSHA, repo3.Name)
|
||||
// Test using org repo "org3/repo3" with no user token
|
||||
req = NewRequestf(t, "GET", "/api/v1/repos/%s/%s/git/blobs/%s", org3.Name, repo3ReadmeSHA, repo3.Name)
|
||||
MakeRequest(t, req, http.StatusNotFound)
|
||||
|
||||
// Login as User4.
|
||||
session = loginUser(t, user4.Name)
|
||||
token4 := getTokenForLoggedInUser(t, session)
|
||||
|
||||
// Test using org repo "user3/repo3" where user4 is a NOT collaborator
|
||||
req = NewRequestf(t, "GET", "/api/v1/repos/%s/%s/git/blobs/d56a3073c1dbb7b15963110a049d50cdb5db99fc?access=%s", user3.Name, repo3.Name, token4)
|
||||
// Test using org repo "org3/repo3" where user4 is a NOT collaborator
|
||||
req = NewRequestf(t, "GET", "/api/v1/repos/%s/%s/git/blobs/d56a3073c1dbb7b15963110a049d50cdb5db99fc?access=%s", org3.Name, repo3.Name, token4)
|
||||
MakeRequest(t, req, http.StatusNotFound)
|
||||
}
|
||||
|
|
|
|||
|
|
@ -17,7 +17,7 @@ import (
|
|||
func TestAPIReposGitTrees(t *testing.T) {
|
||||
defer tests.PrepareTestEnv(t)()
|
||||
user2 := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 2}) // owner of the repo1 & repo16
|
||||
user3 := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 3}) // owner of the repo3
|
||||
org3 := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 3}) // owner of the repo3
|
||||
user4 := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 4}) // owner of neither repos
|
||||
repo1 := unittest.AssertExistsAndLoadBean(t, &repo_model.Repository{ID: 1}) // public repo
|
||||
repo3 := unittest.AssertExistsAndLoadBean(t, &repo_model.Repository{ID: 3}) // public repo
|
||||
|
|
@ -57,19 +57,19 @@ func TestAPIReposGitTrees(t *testing.T) {
|
|||
req = NewRequestf(t, "GET", "/api/v1/repos/%s/%s/git/trees/%s", user2.Name, repo1.Name, badSHA)
|
||||
MakeRequest(t, req, http.StatusBadRequest)
|
||||
|
||||
// Test using org repo "user3/repo3" where user2 is a collaborator
|
||||
req = NewRequestf(t, "GET", "/api/v1/repos/%s/%s/git/trees/%s?token=%s", user3.Name, repo3.Name, repo3TreeSHA, token)
|
||||
// Test using org repo "org3/repo3" where user2 is a collaborator
|
||||
req = NewRequestf(t, "GET", "/api/v1/repos/%s/%s/git/trees/%s?token=%s", org3.Name, repo3.Name, repo3TreeSHA, token)
|
||||
MakeRequest(t, req, http.StatusOK)
|
||||
|
||||
// Test using org repo "user3/repo3" with no user token
|
||||
req = NewRequestf(t, "GET", "/api/v1/repos/%s/%s/git/trees/%s", user3.Name, repo3TreeSHA, repo3.Name)
|
||||
// Test using org repo "org3/repo3" with no user token
|
||||
req = NewRequestf(t, "GET", "/api/v1/repos/%s/%s/git/trees/%s", org3.Name, repo3TreeSHA, repo3.Name)
|
||||
MakeRequest(t, req, http.StatusNotFound)
|
||||
|
||||
// Login as User4.
|
||||
session = loginUser(t, user4.Name)
|
||||
token4 := getTokenForLoggedInUser(t, session)
|
||||
|
||||
// Test using org repo "user3/repo3" where user4 is a NOT collaborator
|
||||
req = NewRequestf(t, "GET", "/api/v1/repos/%s/%s/git/trees/d56a3073c1dbb7b15963110a049d50cdb5db99fc?access=%s", user3.Name, repo3.Name, token4)
|
||||
// Test using org repo "org3/repo3" where user4 is a NOT collaborator
|
||||
req = NewRequestf(t, "GET", "/api/v1/repos/%s/%s/git/trees/d56a3073c1dbb7b15963110a049d50cdb5db99fc?access=%s", org3.Name, repo3.Name, token4)
|
||||
MakeRequest(t, req, http.StatusNotFound)
|
||||
}
|
||||
|
|
|
|||
|
|
@ -23,7 +23,7 @@ import (
|
|||
func TestAPIRepoTeams(t *testing.T) {
|
||||
defer tests.PrepareTestEnv(t)()
|
||||
|
||||
// publicOrgRepo = user3/repo21
|
||||
// publicOrgRepo = org3/repo21
|
||||
publicOrgRepo := unittest.AssertExistsAndLoadBean(t, &repo_model.Repository{ID: 32})
|
||||
// user4
|
||||
user := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 4})
|
||||
|
|
|
|||
|
|
@ -69,7 +69,7 @@ func TestAPISearchRepo(t *testing.T) {
|
|||
|
||||
user := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 15})
|
||||
user2 := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 16})
|
||||
user3 := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 18})
|
||||
org3 := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 18})
|
||||
user4 := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 20})
|
||||
orgUser := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 17})
|
||||
|
||||
|
|
@ -140,11 +140,11 @@ func TestAPISearchRepo(t *testing.T) {
|
|||
},
|
||||
},
|
||||
{
|
||||
name: "RepositoriesAccessibleAndRelatedToUser3", requestURL: fmt.Sprintf("/api/v1/repos/search?uid=%d", user3.ID), expectedResults: expectedResults{
|
||||
name: "RepositoriesAccessibleAndRelatedToUser3", requestURL: fmt.Sprintf("/api/v1/repos/search?uid=%d", org3.ID), expectedResults: expectedResults{
|
||||
nil: {count: 1},
|
||||
user: {count: 4, includesPrivate: true},
|
||||
user2: {count: 3, includesPrivate: true},
|
||||
user3: {count: 4, includesPrivate: true},
|
||||
org3: {count: 4, includesPrivate: true},
|
||||
},
|
||||
},
|
||||
{
|
||||
|
|
@ -289,8 +289,8 @@ func TestAPIOrgRepos(t *testing.T) {
|
|||
defer tests.PrepareTestEnv(t)()
|
||||
user := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 2})
|
||||
user2 := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 1})
|
||||
user3 := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 5})
|
||||
// User3 is an Org. Check their repos.
|
||||
org3 := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 5})
|
||||
// org3 is an Org. Check their repos.
|
||||
sourceOrg := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 3})
|
||||
|
||||
expectedResults := map[*user_model.User]struct {
|
||||
|
|
@ -300,7 +300,7 @@ func TestAPIOrgRepos(t *testing.T) {
|
|||
user: {count: 1},
|
||||
user: {count: 3, includesPrivate: true},
|
||||
user2: {count: 3, includesPrivate: true},
|
||||
user3: {count: 1},
|
||||
org3: {count: 1},
|
||||
}
|
||||
|
||||
for userToLogin, expected := range expectedResults {
|
||||
|
|
@ -438,11 +438,11 @@ func TestAPIOrgRepoCreate(t *testing.T) {
|
|||
orgName, repoName string
|
||||
expectedStatus int
|
||||
}{
|
||||
{ctxUserID: 1, orgName: "user3", repoName: "repo-admin", expectedStatus: http.StatusCreated},
|
||||
{ctxUserID: 2, orgName: "user3", repoName: "repo-own", expectedStatus: http.StatusCreated},
|
||||
{ctxUserID: 2, orgName: "user6", repoName: "repo-bad-org", expectedStatus: http.StatusForbidden},
|
||||
{ctxUserID: 28, orgName: "user3", repoName: "repo-creator", expectedStatus: http.StatusCreated},
|
||||
{ctxUserID: 28, orgName: "user6", repoName: "repo-not-creator", expectedStatus: http.StatusForbidden},
|
||||
{ctxUserID: 1, orgName: "org3", repoName: "repo-admin", expectedStatus: http.StatusCreated},
|
||||
{ctxUserID: 2, orgName: "org3", repoName: "repo-own", expectedStatus: http.StatusCreated},
|
||||
{ctxUserID: 2, orgName: "org6", repoName: "repo-bad-org", expectedStatus: http.StatusForbidden},
|
||||
{ctxUserID: 28, orgName: "org3", repoName: "repo-creator", expectedStatus: http.StatusCreated},
|
||||
{ctxUserID: 28, orgName: "org6", repoName: "repo-not-creator", expectedStatus: http.StatusForbidden},
|
||||
}
|
||||
|
||||
defer tests.PrepareTestEnv(t)()
|
||||
|
|
@ -491,21 +491,21 @@ func TestAPIRepoTransfer(t *testing.T) {
|
|||
teams *[]int64
|
||||
expectedStatus int
|
||||
}{
|
||||
// Disclaimer for test story: "user1" is an admin, "user2" is normal user and part of in owner team of org "user3"
|
||||
// Disclaimer for test story: "user1" is an admin, "user2" is normal user and part of in owner team of org "org3"
|
||||
// Transfer to a user with teams in another org should fail
|
||||
{ctxUserID: 1, newOwner: "user3", teams: &[]int64{5}, expectedStatus: http.StatusForbidden},
|
||||
{ctxUserID: 1, newOwner: "org3", teams: &[]int64{5}, expectedStatus: http.StatusForbidden},
|
||||
// Transfer to a user with non-existent team IDs should fail
|
||||
{ctxUserID: 1, newOwner: "user2", teams: &[]int64{2}, expectedStatus: http.StatusUnprocessableEntity},
|
||||
// Transfer should go through
|
||||
{ctxUserID: 1, newOwner: "user3", teams: &[]int64{2}, expectedStatus: http.StatusAccepted},
|
||||
{ctxUserID: 1, newOwner: "org3", teams: &[]int64{2}, expectedStatus: http.StatusAccepted},
|
||||
// Let user transfer it back to himself
|
||||
{ctxUserID: 2, newOwner: "user2", expectedStatus: http.StatusAccepted},
|
||||
// And revert transfer
|
||||
{ctxUserID: 2, newOwner: "user3", teams: &[]int64{2}, expectedStatus: http.StatusAccepted},
|
||||
{ctxUserID: 2, newOwner: "org3", teams: &[]int64{2}, expectedStatus: http.StatusAccepted},
|
||||
// Cannot start transfer to an existing repo
|
||||
{ctxUserID: 2, newOwner: "user3", teams: nil, expectedStatus: http.StatusUnprocessableEntity},
|
||||
{ctxUserID: 2, newOwner: "org3", teams: nil, expectedStatus: http.StatusUnprocessableEntity},
|
||||
// Start transfer, repo is now in pending transfer mode
|
||||
{ctxUserID: 2, newOwner: "user6", teams: nil, expectedStatus: http.StatusCreated},
|
||||
{ctxUserID: 2, newOwner: "org6", teams: nil, expectedStatus: http.StatusCreated},
|
||||
}
|
||||
|
||||
defer tests.PrepareTestEnv(t)()
|
||||
|
|
@ -648,7 +648,7 @@ func TestAPIGenerateRepo(t *testing.T) {
|
|||
|
||||
// org
|
||||
req = NewRequestWithJSON(t, "POST", fmt.Sprintf("/api/v1/repos/%s/%s/generate?token=%s", templateRepo.OwnerName, templateRepo.Name, token), &api.GenerateRepoOption{
|
||||
Owner: "user3",
|
||||
Owner: "org3",
|
||||
Name: "new-repo",
|
||||
Description: "test generate repo",
|
||||
Private: false,
|
||||
|
|
|
|||
|
|
@ -54,7 +54,7 @@ func TestAPITopicSearch(t *testing.T) {
|
|||
func TestAPIRepoTopic(t *testing.T) {
|
||||
defer tests.PrepareTestEnv(t)()
|
||||
user2 := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 2}) // owner of repo2
|
||||
user3 := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 3}) // owner of repo3
|
||||
org3 := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 3}) // owner of repo3
|
||||
user4 := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 4}) // write access to repo 3
|
||||
repo2 := unittest.AssertExistsAndLoadBean(t, &repo_model.Repository{ID: 2})
|
||||
repo3 := unittest.AssertExistsAndLoadBean(t, &repo_model.Repository{ID: 3})
|
||||
|
|
@ -143,13 +143,13 @@ func TestAPIRepoTopic(t *testing.T) {
|
|||
token4 := getUserToken(t, user4.Name, auth_model.AccessTokenScopeWriteRepository)
|
||||
|
||||
// Test read topics with write access
|
||||
url = fmt.Sprintf("/api/v1/repos/%s/%s/topics?token=%s", user3.Name, repo3.Name, token4)
|
||||
url = fmt.Sprintf("/api/v1/repos/%s/%s/topics?token=%s", org3.Name, repo3.Name, token4)
|
||||
req = NewRequest(t, "GET", url)
|
||||
res = MakeRequest(t, req, http.StatusOK)
|
||||
DecodeJSON(t, res, &topics)
|
||||
assert.Empty(t, topics.TopicNames)
|
||||
|
||||
// Test add a topic to repo with write access (requires repo admin access)
|
||||
req = NewRequestf(t, "PUT", "/api/v1/repos/%s/%s/topics/%s?token=%s", user3.Name, repo3.Name, "topicName", token4)
|
||||
req = NewRequestf(t, "PUT", "/api/v1/repos/%s/%s/topics/%s?token=%s", org3.Name, repo3.Name, "topicName", token4)
|
||||
MakeRequest(t, req, http.StatusForbidden)
|
||||
}
|
||||
|
|
|
|||
|
|
@ -23,7 +23,7 @@ func TestAPIUserInfo(t *testing.T) {
|
|||
user := "user1"
|
||||
user2 := "user31"
|
||||
|
||||
user3 := unittest.AssertExistsAndLoadBean(t, &user_model.User{Name: "user3"})
|
||||
org3 := unittest.AssertExistsAndLoadBean(t, &user_model.User{Name: "org3"})
|
||||
|
||||
session := loginUser(t, user)
|
||||
token := getTokenForLoggedInUser(t, session, auth_model.AccessTokenScopeReadUser)
|
||||
|
|
@ -42,16 +42,16 @@ func TestAPIUserInfo(t *testing.T) {
|
|||
MakeRequest(t, req, http.StatusNotFound)
|
||||
|
||||
// test if the placaholder Mail is returned if a User is not logged in
|
||||
req = NewRequest(t, "GET", fmt.Sprintf("/api/v1/users/%s", user3.Name))
|
||||
req = NewRequest(t, "GET", fmt.Sprintf("/api/v1/users/%s", org3.Name))
|
||||
resp = MakeRequest(t, req, http.StatusOK)
|
||||
DecodeJSON(t, resp, &u)
|
||||
assert.Equal(t, user3.GetPlaceholderEmail(), u.Email)
|
||||
assert.Equal(t, org3.GetPlaceholderEmail(), u.Email)
|
||||
|
||||
// Test if the correct Mail is returned if a User is logged in
|
||||
req = NewRequest(t, "GET", fmt.Sprintf("/api/v1/users/%s?token=%s", user3.Name, token))
|
||||
req = NewRequest(t, "GET", fmt.Sprintf("/api/v1/users/%s?token=%s", org3.Name, token))
|
||||
resp = MakeRequest(t, req, http.StatusOK)
|
||||
DecodeJSON(t, resp, &u)
|
||||
assert.Equal(t, user3.GetEmail(), u.Email)
|
||||
assert.Equal(t, org3.GetEmail(), u.Email)
|
||||
})
|
||||
|
||||
t.Run("GetAuthenticatedUser", func(t *testing.T) {
|
||||
|
|
|
|||
|
|
@ -25,7 +25,7 @@ type apiUserOrgPermTestCase struct {
|
|||
func TestTokenNeeded(t *testing.T) {
|
||||
defer tests.PrepareTestEnv(t)()
|
||||
|
||||
req := NewRequest(t, "GET", "/api/v1/users/user1/orgs/user6/permissions")
|
||||
req := NewRequest(t, "GET", "/api/v1/users/user1/orgs/org6/permissions")
|
||||
MakeRequest(t, req, http.StatusUnauthorized)
|
||||
}
|
||||
|
||||
|
|
@ -51,7 +51,7 @@ func TestWithOwnerUser(t *testing.T) {
|
|||
sampleTest(t, apiUserOrgPermTestCase{
|
||||
LoginUser: "user2",
|
||||
User: "user2",
|
||||
Organization: "user3",
|
||||
Organization: "org3",
|
||||
ExpectedOrganizationPermissions: api.OrganizationPermissions{
|
||||
IsOwner: true,
|
||||
IsAdmin: true,
|
||||
|
|
@ -66,7 +66,7 @@ func TestCanWriteUser(t *testing.T) {
|
|||
sampleTest(t, apiUserOrgPermTestCase{
|
||||
LoginUser: "user4",
|
||||
User: "user4",
|
||||
Organization: "user3",
|
||||
Organization: "org3",
|
||||
ExpectedOrganizationPermissions: api.OrganizationPermissions{
|
||||
IsOwner: false,
|
||||
IsAdmin: false,
|
||||
|
|
@ -81,7 +81,7 @@ func TestAdminUser(t *testing.T) {
|
|||
sampleTest(t, apiUserOrgPermTestCase{
|
||||
LoginUser: "user1",
|
||||
User: "user28",
|
||||
Organization: "user3",
|
||||
Organization: "org3",
|
||||
ExpectedOrganizationPermissions: api.OrganizationPermissions{
|
||||
IsOwner: false,
|
||||
IsAdmin: true,
|
||||
|
|
@ -96,7 +96,7 @@ func TestAdminCanNotCreateRepo(t *testing.T) {
|
|||
sampleTest(t, apiUserOrgPermTestCase{
|
||||
LoginUser: "user1",
|
||||
User: "user28",
|
||||
Organization: "user6",
|
||||
Organization: "org6",
|
||||
ExpectedOrganizationPermissions: api.OrganizationPermissions{
|
||||
IsOwner: false,
|
||||
IsAdmin: true,
|
||||
|
|
|
|||
|
|
@ -27,17 +27,17 @@ func TestUserOrgs(t *testing.T) {
|
|||
|
||||
orgs := getUserOrgs(t, adminUsername, normalUsername)
|
||||
|
||||
user3 := unittest.AssertExistsAndLoadBean(t, &user_model.User{Name: "user3"})
|
||||
user17 := unittest.AssertExistsAndLoadBean(t, &user_model.User{Name: "user17"})
|
||||
org3 := unittest.AssertExistsAndLoadBean(t, &user_model.User{Name: "org3"})
|
||||
org17 := unittest.AssertExistsAndLoadBean(t, &user_model.User{Name: "org17"})
|
||||
|
||||
assert.Equal(t, []*api.Organization{
|
||||
{
|
||||
ID: 17,
|
||||
Name: user17.Name,
|
||||
UserName: user17.Name,
|
||||
FullName: user17.FullName,
|
||||
Email: user17.Email,
|
||||
AvatarURL: user17.AvatarLink(db.DefaultContext),
|
||||
Name: org17.Name,
|
||||
UserName: org17.Name,
|
||||
FullName: org17.FullName,
|
||||
Email: org17.Email,
|
||||
AvatarURL: org17.AvatarLink(db.DefaultContext),
|
||||
Description: "",
|
||||
Website: "",
|
||||
Location: "",
|
||||
|
|
@ -45,11 +45,11 @@ func TestUserOrgs(t *testing.T) {
|
|||
},
|
||||
{
|
||||
ID: 3,
|
||||
Name: user3.Name,
|
||||
UserName: user3.Name,
|
||||
FullName: user3.FullName,
|
||||
Email: user3.Email,
|
||||
AvatarURL: user3.AvatarLink(db.DefaultContext),
|
||||
Name: org3.Name,
|
||||
UserName: org3.Name,
|
||||
FullName: org3.FullName,
|
||||
Email: org3.Email,
|
||||
AvatarURL: org3.AvatarLink(db.DefaultContext),
|
||||
Description: "",
|
||||
Website: "",
|
||||
Location: "",
|
||||
|
|
@ -99,17 +99,17 @@ func TestMyOrgs(t *testing.T) {
|
|||
resp := MakeRequest(t, req, http.StatusOK)
|
||||
var orgs []*api.Organization
|
||||
DecodeJSON(t, resp, &orgs)
|
||||
user3 := unittest.AssertExistsAndLoadBean(t, &user_model.User{Name: "user3"})
|
||||
user17 := unittest.AssertExistsAndLoadBean(t, &user_model.User{Name: "user17"})
|
||||
org3 := unittest.AssertExistsAndLoadBean(t, &user_model.User{Name: "org3"})
|
||||
org17 := unittest.AssertExistsAndLoadBean(t, &user_model.User{Name: "org17"})
|
||||
|
||||
assert.Equal(t, []*api.Organization{
|
||||
{
|
||||
ID: 17,
|
||||
Name: user17.Name,
|
||||
UserName: user17.Name,
|
||||
FullName: user17.FullName,
|
||||
Email: user17.Email,
|
||||
AvatarURL: user17.AvatarLink(db.DefaultContext),
|
||||
Name: org17.Name,
|
||||
UserName: org17.Name,
|
||||
FullName: org17.FullName,
|
||||
Email: org17.Email,
|
||||
AvatarURL: org17.AvatarLink(db.DefaultContext),
|
||||
Description: "",
|
||||
Website: "",
|
||||
Location: "",
|
||||
|
|
@ -117,11 +117,11 @@ func TestMyOrgs(t *testing.T) {
|
|||
},
|
||||
{
|
||||
ID: 3,
|
||||
Name: user3.Name,
|
||||
UserName: user3.Name,
|
||||
FullName: user3.FullName,
|
||||
Email: user3.Email,
|
||||
AvatarURL: user3.AvatarLink(db.DefaultContext),
|
||||
Name: org3.Name,
|
||||
UserName: org3.Name,
|
||||
FullName: org3.FullName,
|
||||
Email: org3.Email,
|
||||
AvatarURL: org3.AvatarLink(db.DefaultContext),
|
||||
Description: "",
|
||||
Website: "",
|
||||
Location: "",
|
||||
|
|
|
|||
|
|
@ -432,14 +432,14 @@ func TestSearchIssues(t *testing.T) {
|
|||
DecodeJSON(t, resp, &apiIssues)
|
||||
assert.Len(t, apiIssues, 8)
|
||||
|
||||
query = url.Values{"owner": {"user3"}} // organization
|
||||
query = url.Values{"owner": {"org3"}} // organization
|
||||
link.RawQuery = query.Encode()
|
||||
req = NewRequest(t, "GET", link.String())
|
||||
resp = session.MakeRequest(t, req, http.StatusOK)
|
||||
DecodeJSON(t, resp, &apiIssues)
|
||||
assert.Len(t, apiIssues, 5)
|
||||
|
||||
query = url.Values{"owner": {"user3"}, "team": {"team1"}} // organization + team
|
||||
query = url.Values{"owner": {"org3"}, "team": {"team1"}} // organization + team
|
||||
link.RawQuery = query.Encode()
|
||||
req = NewRequest(t, "GET", link.String())
|
||||
resp = session.MakeRequest(t, req, http.StatusOK)
|
||||
|
|
|
|||
|
|
@ -26,27 +26,27 @@ func TestOrgProjectAccess(t *testing.T) {
|
|||
MakeRequest(t, req, http.StatusOK)
|
||||
|
||||
// org project, 200
|
||||
req = NewRequest(t, "GET", "/user3/-/projects")
|
||||
req = NewRequest(t, "GET", "/org3/-/projects")
|
||||
MakeRequest(t, req, http.StatusOK)
|
||||
|
||||
// change the org's visibility to private
|
||||
session := loginUser(t, "user2")
|
||||
req = NewRequestWithValues(t, "POST", "/org/user3/settings", map[string]string{
|
||||
"_csrf": GetCSRF(t, session, "/user3/-/projects"),
|
||||
"name": "user3",
|
||||
req = NewRequestWithValues(t, "POST", "/org/org3/settings", map[string]string{
|
||||
"_csrf": GetCSRF(t, session, "/org3/-/projects"),
|
||||
"name": "org3",
|
||||
"visibility": "2",
|
||||
})
|
||||
session.MakeRequest(t, req, http.StatusSeeOther)
|
||||
|
||||
// user4 can still access the org's project because its team(team1) has the permission
|
||||
session = loginUser(t, "user4")
|
||||
req = NewRequest(t, "GET", "/user3/-/projects")
|
||||
req = NewRequest(t, "GET", "/org3/-/projects")
|
||||
session.MakeRequest(t, req, http.StatusOK)
|
||||
|
||||
// disable team1's project unit
|
||||
session = loginUser(t, "user2")
|
||||
req = NewRequestWithValues(t, "POST", "/org/user3/teams/team1/edit", map[string]string{
|
||||
"_csrf": GetCSRF(t, session, "/user3/-/projects"),
|
||||
req = NewRequestWithValues(t, "POST", "/org/org3/teams/team1/edit", map[string]string{
|
||||
"_csrf": GetCSRF(t, session, "/org3/-/projects"),
|
||||
"team_name": "team1",
|
||||
"repo_access": "specific",
|
||||
"permission": "read",
|
||||
|
|
@ -56,6 +56,6 @@ func TestOrgProjectAccess(t *testing.T) {
|
|||
|
||||
// user4 can no longer access the org's project
|
||||
session = loginUser(t, "user4")
|
||||
req = NewRequest(t, "GET", "/user3/-/projects")
|
||||
req = NewRequest(t, "GET", "/org3/-/projects")
|
||||
session.MakeRequest(t, req, http.StatusNotFound)
|
||||
}
|
||||
|
|
|
|||
|
|
@ -33,7 +33,7 @@ func TestOrgRepos(t *testing.T) {
|
|||
t.Run(user, func(t *testing.T) {
|
||||
session := loginUser(t, user)
|
||||
for sortBy, repos := range cases {
|
||||
req := NewRequest(t, "GET", "/user3?sort="+sortBy)
|
||||
req := NewRequest(t, "GET", "/org3?sort="+sortBy)
|
||||
resp := session.MakeRequest(t, req, http.StatusOK)
|
||||
|
||||
htmlDoc := NewHTMLParser(t, resp.Body)
|
||||
|
|
|
|||
|
|
@ -24,7 +24,7 @@ const (
|
|||
privateActivityTestUser = "user2"
|
||||
)
|
||||
|
||||
// user3 is an organization so it is not usable here
|
||||
// org3 is an organization so it is not usable here
|
||||
const privateActivityTestOtherUser = "user4"
|
||||
|
||||
// activity helpers
|
||||
|
|
|
|||
|
|
@ -63,10 +63,10 @@ func TestRepoFork(t *testing.T) {
|
|||
func TestRepoForkToOrg(t *testing.T) {
|
||||
defer tests.PrepareTestEnv(t)()
|
||||
session := loginUser(t, "user2")
|
||||
testRepoFork(t, session, "user2", "repo1", "user3", "repo1")
|
||||
testRepoFork(t, session, "user2", "repo1", "org3", "repo1")
|
||||
|
||||
// Check that no more forking is allowed as user2 owns repository
|
||||
// and user3 organization that owner user2 is also now has forked this repository
|
||||
// and org3 organization that owner user2 is also now has forked this repository
|
||||
req := NewRequest(t, "GET", "/user2/repo1")
|
||||
resp := session.MakeRequest(t, req, http.StatusOK)
|
||||
htmlDoc := NewHTMLParser(t, resp.Body)
|
||||
|
|
|
|||
|
|
@ -35,7 +35,7 @@ func TestViewRepo(t *testing.T) {
|
|||
assert.True(t, repoTopics.HasClass("repo-topic"))
|
||||
assert.True(t, repoSummary.HasClass("repository-menu"))
|
||||
|
||||
req = NewRequest(t, "GET", "/user3/repo3")
|
||||
req = NewRequest(t, "GET", "/org3/repo3")
|
||||
MakeRequest(t, req, http.StatusNotFound)
|
||||
|
||||
session = loginUser(t, "user1")
|
||||
|
|
@ -45,7 +45,7 @@ func TestViewRepo(t *testing.T) {
|
|||
func testViewRepo(t *testing.T) {
|
||||
defer tests.PrepareTestEnv(t)()
|
||||
|
||||
req := NewRequest(t, "GET", "/user3/repo3")
|
||||
req := NewRequest(t, "GET", "/org3/repo3")
|
||||
session := loginUser(t, "user2")
|
||||
resp := session.MakeRequest(t, req, http.StatusOK)
|
||||
|
||||
|
|
@ -116,7 +116,7 @@ func TestViewRepo2(t *testing.T) {
|
|||
func TestViewRepo3(t *testing.T) {
|
||||
defer tests.PrepareTestEnv(t)()
|
||||
|
||||
req := NewRequest(t, "GET", "/user3/repo3")
|
||||
req := NewRequest(t, "GET", "/org3/repo3")
|
||||
session := loginUser(t, "user4")
|
||||
session.MakeRequest(t, req, http.StatusOK)
|
||||
}
|
||||
|
|
|
|||
|
|
@ -18,7 +18,7 @@ func TestRepoWatch(t *testing.T) {
|
|||
setting.Service.AutoWatchOnChanges = true
|
||||
session := loginUser(t, "user2")
|
||||
unittest.AssertNotExistsBean(t, &repo_model.Watch{UserID: 2, RepoID: 3})
|
||||
testEditFile(t, session, "user3", "repo3", "master", "README.md", "Hello, World (Edited for watch)\n")
|
||||
testEditFile(t, session, "org3", "repo3", "master", "README.md", "Hello, World (Edited for watch)\n")
|
||||
unittest.AssertExistsAndLoadBean(t, &repo_model.Watch{UserID: 2, RepoID: 3, Mode: repo_model.WatchModeAuto})
|
||||
})
|
||||
}
|
||||
|
|
|
|||
|
|
@ -32,7 +32,7 @@ func TestNotViewTimetrackingControls(t *testing.T) {
|
|||
func TestViewTimetrackingControlsDisabled(t *testing.T) {
|
||||
defer tests.PrepareTestEnv(t)()
|
||||
session := loginUser(t, "user2")
|
||||
testViewTimetrackingControls(t, session, "user3", "repo3", "1", false)
|
||||
testViewTimetrackingControls(t, session, "org3", "repo3", "1", false)
|
||||
}
|
||||
|
||||
func testViewTimetrackingControls(t *testing.T, session *TestSession, user, repo, issue string, canTrackTime bool) {
|
||||
|
|
|
|||
|
|
@ -6,10 +6,10 @@ window.config = {
|
|||
mentionValues: [
|
||||
{key: 'user1 User 1', value: 'user1', name: 'user1', fullname: 'User 1', avatar: 'https://avatar1.com'},
|
||||
{key: 'user2 User 2', value: 'user2', name: 'user2', fullname: 'User 2', avatar: 'https://avatar2.com'},
|
||||
{key: 'user3 User 3', value: 'user3', name: 'user3', fullname: 'User 3', avatar: 'https://avatar3.com'},
|
||||
{key: 'org3 User 3', value: 'org3', name: 'org3', fullname: 'User 3', avatar: 'https://avatar3.com'},
|
||||
{key: 'user4 User 4', value: 'user4', name: 'user4', fullname: 'User 4', avatar: 'https://avatar4.com'},
|
||||
{key: 'user5 User 5', value: 'user5', name: 'user5', fullname: 'User 5', avatar: 'https://avatar5.com'},
|
||||
{key: 'user6 User 6', value: 'user6', name: 'user6', fullname: 'User 6', avatar: 'https://avatar6.com'},
|
||||
{key: 'user7 User 7', value: 'user7', name: 'user7', fullname: 'User 7', avatar: 'https://avatar7.com'},
|
||||
{key: 'org6 User 6', value: 'org6', name: 'org6', fullname: 'User 6', avatar: 'https://avatar6.com'},
|
||||
{key: 'org7 User 7', value: 'org7', name: 'org7', fullname: 'User 7', avatar: 'https://avatar7.com'},
|
||||
],
|
||||
};
|
||||
|
|
|
|||
Loading…
Add table
Add a link
Reference in a new issue